Personal cheques are available on U.S. Dollar chequing accounts with us, however, they are encoded for clearance through the Canadian clearing system only. You may have difficulty clearing the cheques through the U.S.
clearing system. This is due to changes in U.S. Federal banking regulations. However, you do have alternatives.
The first alternative is to purchase U.S. Dollar drafts at the branch. If you have the Borderless service set up on your account (for $4.95 per month with unlimited transactions), U.S. Dollar drafts are free. If you do not have the Borderless service, U.S. Dollar drafts can be purchased for $6.50 (you'll also have to pay $1.00 for each individual transaction). This would be the most economical way to send funds to the United States. Information about the Borderless service can be found at:
http://www.tdcanadatrust.com/accounts/usaccount.jsp
Another alternative would be to send an electronic wire transfer. This option is costlier and you will be charged $30.00 to $50.00 per transfer.
However, an electronic transfer is very fast and should arrive in the beneficiary account within a few business days.
If your payments in the United States can be completed via credit card, then please feel free to view the information about the TD U.S. Dollar Advantage Visa and apply on-line through the following address:
http://www.tdcanadatrust.com/tdvisa/usd.jsp
You also have the option of opening a U.S. Dollar account at TD Waterhouse Bank, our U.S. subsidiary. TD Waterhouse Bank is an affiliated bank in the United States that offers chequing accounts. More detailed information can be found at:
http://www.tdwaterhouse.com/banking/welcome/index.html
Regular Traveller's Cheques are available for Borderless service account holders with no commission fee. The commission if you don't have the Borderless service is 1%. The commission fee for dual signature cheques is 1.75%.
Cheques for a U.S. Dollar account are free (basic style, personalized) if you have the Borderless service. If not, an order of cheques will cost about $15.00 to $20.00 depending on your provice of residence, with shipping and handling and taxes included.
Thursday, September 30, 2010
Wednesday, September 29, 2010
SQL query perfomance check method
you can check that how long each query takes to run... this should give you some idea which one performs better...
Code Snippet
DBCC DROPCLEANBUFFERS
SET STATISTICS IO ON
SET STATISTICS TIME ON
select top 10000 * from Table
SET STATISTICS TIME OFF
SET STATISTICS IO OFF
DBCC DROPCLEANBUFFERS
SET STATISTICS IO ON
SET STATISTICS TIME ON
Set rowcount 10000
Select * From Table
SET STATISTICS TIME OFF
SET STATISTICS IO OFF
Tuesday, September 28, 2010
SQL SERVER – Insert Data From One Table to Another Table – INSERT INTO SELECT – SELECT INTO TABLE
Following three questions are many time asked on this blog.
How to insert data from one table to another table efficiently?
How to insert data from one table using where condition to anther table?
How can I stop using cursor to move data from one table to another table?
How to insert data from one table using where condition to anther table?
How can I stop using cursor to move data from one table to another table?
There are two different ways to implement inserting data from one table to another table. I strongly suggest to use either of the method over cursor. Performance of following two methods is far superior over cursor. I prefer to use Method 1 always as I works in all the case.
Method 1 : INSERT INTO SELECT
This method is used when table is already created in the database earlier and data is to be inserted into this table from another table. If columns listed in insert clause and select clause are same, they are are not required to list them. I always list them for readability and scalability purpose.
Method 2 : SELECT INTO
This method is used when table is not created earlier and needs to be created when data from one table is to be inserted into newly created table from another table. New table is created with same data types as selected columns.
Both of the above method works with database temporary tables (global, local). If you want to insert multiple rows using only one insert statement refer article SQL SERVER – Insert Multiple Records Using One Insert Statement – Use of UNION ALL.
This method is used when table is already created in the database earlier and data is to be inserted into this table from another table. If columns listed in insert clause and select clause are same, they are are not required to list them. I always list them for readability and scalability purpose.
USE AdventureWorks
GO
----Create TestTable
CREATE TABLE TestTable (FirstName VARCHAR(100), LastName VARCHAR(100))
----INSERT INTO TestTable using SELECT
INSERT INTO TestTable (FirstName, LastName)
SELECT FirstName, LastName
FROM Person.Contact
WHERE EmailPromotion = 2
----Verify that Data in TestTable
SELECT FirstName, LastName
FROM TestTable
----Clean Up Database
DROP TABLE TestTable
GO
Method 2 : SELECT INTO
This method is used when table is not created earlier and needs to be created when data from one table is to be inserted into newly created table from another table. New table is created with same data types as selected columns.
USE AdventureWorks
GO
----Create new table and insert into table using SELECT INSERT
SELECT FirstName, LastName
INTO TestTable
FROM Person.Contact
WHERE EmailPromotion = 2
----Verify that Data in TestTable
SELECT FirstName, LastName
FROM TestTable
----Clean Up Database
DROP TABLE TestTable
GO
Both of the above method works with database temporary tables (global, local). If you want to insert multiple rows using only one insert statement refer article SQL SERVER – Insert Multiple Records Using One Insert Statement – Use of UNION ALL.
source: http://blog.sqlauthority.com/2007/08/15/sql-server-insert-data-from-one-table-to-another-table-insert-into-select-select-into-table/
Solve ‘String or binary data would be truncated’ sql error
The error ‘String or binary data would be truncated’ can be annoying. It occurs when you try to insert or update a string or binary column with a value that is too large. Recently I was trying to INSERT from a SELECT from one table to another and I got this error. It can be a pain tracking down the cause, especially if there are a large number of columns or a large dataset involved.
In the past I’ve written queries to give me the LEN for each column, but again if there are a large number of columns involved this can be very time consuming.
Below is a way of identifying which rows are causing the problem. This doesn’t help if you’ve got a large number of columns, as you still need to work out which field is causing the problem, but it will help if you have a large dataset and the problem rows are very sparse.
For this example I’ll create a couple of tables and generate some data. The source table has a column of VARCHAR(50), whereas the destination has VARCHAR(25):
It’s possible to ignore the 'String or binary data would be truncated' message by setting ANSI_WARNINGS to OFF. This will truncate fields where they don’t fit. ANSI_WARNINGS OFF has drawbacks and it is better to correct a problem rather than ignore it.
The following can be used to work out which rows are causing the issue:
1. Take a copy of the destination table:
2. Set ANSI_WARNINGS OFF and perform the insert into the copy of the destination table, then set ANSI_WARNINGS ON again:
As ANSI_WARNINGS is off SQL Server truncates the fields rather than produces the warning.
3. Next compare what you would like to insert against what was inserted with the ANSI_WARNINGS OFF truncating. By using EXCEPT you only select the rows that don't match, and have therefore been truncated:
The rows that have been truncated and are the cause of the ‘String or binary data would be truncated’ error.
(Note - The use of EXCEPT limits this to 2005/2008. The finaly query could be re-written for SQL Server 2000 and below.)
This isn’t the most elegant solution, and as I said if there were a large number of columns you’d still need to hunt through for the offender(s), but at least this gives an idea of where to look. I may have missed some glaringly obvious solution to this problem, so I’d be interested to know if anyone has any other ways of dealing it.
source: http://sqlblogcasts.com/blogs/danny/archive/2008/01/12/scuffling-with-string-or-binary-data-would-be-truncated.aspx
In the past I’ve written queries to give me the LEN for each column, but again if there are a large number of columns involved this can be very time consuming.
Below is a way of identifying which rows are causing the problem. This doesn’t help if you’ve got a large number of columns, as you still need to work out which field is causing the problem, but it will help if you have a large dataset and the problem rows are very sparse.
For this example I’ll create a couple of tables and generate some data. The source table has a column of VARCHAR(50), whereas the destination has VARCHAR(25):
CREATE TABLE SourceTable
(
RowId INT
,Chars INT
,String VARCHAR(50)
)
GO
CREATE TABLE DestinationTable
(
RowId INT
,Chars INT
,String VARCHAR(25)
)
GO
Next the tables are populated with a random number of ‘X’s, between 0 and 50. In theory you should get about 50% with a length above 25 characters and 50% below.DECLARE @i INT
DECLARE @RandomNumber INT
SET @i=0
WHILE @i <= 50
BEGIN
SET @RandomNumber = ROUND(50 * RAND(), 0)
INSERT INTO SourceTable
SELECT @i, @RandomNumber, REPLICATE('X', @RandomNumber)
SET @i=@i+1
END
GO
Next try inserting from SourceTable to DestinationTable:
INSERT INTO DestinationTable
SELECT * FROM SourceTableGO
This results in the error:Msg 8152, Level 16, State 14, Line 1
String or binary data would be truncated.
The statement has been terminated.
It’s possible to ignore the 'String or binary data would be truncated' message by setting ANSI_WARNINGS to OFF. This will truncate fields where they don’t fit. ANSI_WARNINGS OFF has drawbacks and it is better to correct a problem rather than ignore it.
The following can be used to work out which rows are causing the issue:
1. Take a copy of the destination table:
SELECT * INTO #Destination FROM DestinationTable WHERE 1=2
GO
2. Set ANSI_WARNINGS OFF and perform the insert into the copy of the destination table, then set ANSI_WARNINGS ON again:
SET ANSI_WARNINGS OFF
GO
INSERT INTO #Destination
SELECT * FROM SourceTable
GO
SET ANSI_WARNINGS ON
GO
As ANSI_WARNINGS is off SQL Server truncates the fields rather than produces the warning.
3. Next compare what you would like to insert against what was inserted with the ANSI_WARNINGS OFF truncating. By using EXCEPT you only select the rows that don't match, and have therefore been truncated:
SELECT * FROM SourceTable
EXCEPT
SELECT * FROM #Destination
GO
The rows that have been truncated and are the cause of the ‘String or binary data would be truncated’ error.
(Note - The use of EXCEPT limits this to 2005/2008. The finaly query could be re-written for SQL Server 2000 and below.)
This isn’t the most elegant solution, and as I said if there were a large number of columns you’d still need to hunt through for the offender(s), but at least this gives an idea of where to look. I may have missed some glaringly obvious solution to this problem, so I’d be interested to know if anyone has any other ways of dealing it.
source: http://sqlblogcasts.com/blogs/danny/archive/2008/01/12/scuffling-with-string-or-binary-data-would-be-truncated.aspx
Friday, September 24, 2010
子网(subnet)掩码计算的几个理解方法
1.
69.65.53.96/29 子网掩码多少(Ans:255.255.255.248)
----------------------------------------------------------------------
2.
192.168.0.0/29 29个1 11111111 11111111 11111111 11111000 掩码是255.255.255.248
192.168.0.0/22 22个1 11111111 11111111 11111100 00000000 掩码是255.255.252.0
29个1可知主机位占3 位即2的3次方-2个主机所以每个子网内有6台主机。子网位占5位,2的5次方-2个子网,得30个子网。地址段:192.168.0.9---14、192.168.17---22,,,,,
22个1 可知主机位占10位,得2的10次方-2个主机,子网位占6位得2 的6次方-2个子网
地址段:192.168.4.1---192.168.7.254、192.168.8.1---192.168.11.254、192.168.12.1--192.168.15.254
----------------------------------------------------------------------
3.
子网掩码32就是
8 8 8 8
| | | |
255 255 255 255
子网掩码29就是
8 8 8 5
255 255 255 248
248=128+96+32+16+8
32位的掩码分为四段表示,对应四个十进制数。
29位掩码被32位一减,得3位,2的3次方为8,即十进制中的256-8=248;
22位掩码被32位一减,得10位,应在十进制表示中的第三部分,再减8位得2位,2的2次方为4,256-4=252
----------------------------------------------------------------------
4.只知道10.179.152.113/29,怎么知道网关、掩码和IP。
网关可能是:10.179.152.112
IP是:10.179.152.113
掩码是:255.255.255.248
答案补充
29位掩码就是有29个"1",下面用二进制表示,你数一下:
11111111.11111111.11111111.11111000=255.255.255.248
我说可能是因为多数人的习惯是将第一个可用IP做为网关.
10.179.152.113所在网段为10.179.152.112,所以网关可能是113(前面说112有误)
答案补充
IP可以是114~118中的一个.
-----------------------------------------------------------------
5.一个主机的IP地址是202.112.14.137,掩码是255.255.255.224,要求计算这个主机所在网络的网络地址和广播地址。
常 规办法是把这个主机地址和子网掩码都换算成二进制数,两者进行逻辑与运算后即可得到网络地址。其实大家只要仔细想想,可以得到另一个方 法:255.255.255.224的掩码所容纳的IP地址有256-224=32个(包括网络地址和广播地址),那么具有这种掩码的网络地址一定是32 的倍数。而网络地址是子网IP地址的开始,广播地址是结束,可使用的主机地址在这个范围内,因此略小于137而又是32的倍数的只有128,所以得出网络 地址是202.112.14.128。而广播地址就是下一个网络的网络地址减1。而下一个32的倍数是160,因此可以得到广播地址为 202.112.14.159。
CCNA考试中,还有一种题型,要你根据每个网络的主机数量进行子网地址的规划和计算子网掩码。这也可按上述原则进行计算。比如一个子网有10台主机,那么对于这个子网需要的IP地址是:
10+1+1+1=13
注意:加的第一个1是指这个网络连接时所需的网关地址,接着的两个1分别是指网络地址和广播地址。因为13小于16(16等于2的4次方),所以主机位为4位。而
256-16=240
所以该子网掩码为255.255.255.240。
如果一个子网有14台主机,不少人常犯的错误是:依然分配具有16个地址空间的子网,而忘记了给网关分配地址。这样就错误了,因为:
14+1+1+1=17
于16,所以我们只能分配具有32个地址(32等于2的5次方)空间的子网。这时子网掩码为:255.255.255.224
69.65.53.96/29 子网掩码多少(Ans:255.255.255.248)
----------------------------------------------------------------------
2.
192.168.0.0/29 29个1 11111111 11111111 11111111 11111000 掩码是255.255.255.248
192.168.0.0/22 22个1 11111111 11111111 11111100 00000000 掩码是255.255.252.0
29个1可知主机位占3 位即2的3次方-2个主机所以每个子网内有6台主机。子网位占5位,2的5次方-2个子网,得30个子网。地址段:192.168.0.9---14、192.168.17---22,,,,,
22个1 可知主机位占10位,得2的10次方-2个主机,子网位占6位得2 的6次方-2个子网
地址段:192.168.4.1---192.168.7.254、192.168.8.1---192.168.11.254、192.168.12.1--192.168.15.254
----------------------------------------------------------------------
3.
子网掩码32就是
8 8 8 8
| | | |
255 255 255 255
子网掩码29就是
8 8 8 5
255 255 255 248
248=128+96+32+16+8
32位的掩码分为四段表示,对应四个十进制数。
29位掩码被32位一减,得3位,2的3次方为8,即十进制中的256-8=248;
22位掩码被32位一减,得10位,应在十进制表示中的第三部分,再减8位得2位,2的2次方为4,256-4=252
----------------------------------------------------------------------
4.只知道10.179.152.113/29,怎么知道网关、掩码和IP。
网关可能是:10.179.152.112
IP是:10.179.152.113
掩码是:255.255.255.248
答案补充
29位掩码就是有29个"1",下面用二进制表示,你数一下:
11111111.11111111.11111111.11111000=255.255.255.248
我说可能是因为多数人的习惯是将第一个可用IP做为网关.
10.179.152.113所在网段为10.179.152.112,所以网关可能是113(前面说112有误)
答案补充
IP可以是114~118中的一个.
-----------------------------------------------------------------
5.一个主机的IP地址是202.112.14.137,掩码是255.255.255.224,要求计算这个主机所在网络的网络地址和广播地址。
常 规办法是把这个主机地址和子网掩码都换算成二进制数,两者进行逻辑与运算后即可得到网络地址。其实大家只要仔细想想,可以得到另一个方 法:255.255.255.224的掩码所容纳的IP地址有256-224=32个(包括网络地址和广播地址),那么具有这种掩码的网络地址一定是32 的倍数。而网络地址是子网IP地址的开始,广播地址是结束,可使用的主机地址在这个范围内,因此略小于137而又是32的倍数的只有128,所以得出网络 地址是202.112.14.128。而广播地址就是下一个网络的网络地址减1。而下一个32的倍数是160,因此可以得到广播地址为 202.112.14.159。
CCNA考试中,还有一种题型,要你根据每个网络的主机数量进行子网地址的规划和计算子网掩码。这也可按上述原则进行计算。比如一个子网有10台主机,那么对于这个子网需要的IP地址是:
10+1+1+1=13
注意:加的第一个1是指这个网络连接时所需的网关地址,接着的两个1分别是指网络地址和广播地址。因为13小于16(16等于2的4次方),所以主机位为4位。而
256-16=240
所以该子网掩码为255.255.255.240。
如果一个子网有14台主机,不少人常犯的错误是:依然分配具有16个地址空间的子网,而忘记了给网关分配地址。这样就错误了,因为:
14+1+1+1=17
于16,所以我们只能分配具有32个地址(32等于2的5次方)空间的子网。这时子网掩码为:255.255.255.224
Thursday, September 23, 2010
Move a Table to a Different File Group (ZT)
http://my.advisor.com/doc/16671
Q: We've been having problems with disk space on our SQL Server. I've been deleting old, unimportant data, but that isn't enough. I set up additional hard drive space on a separate drive, and I know how to create a new filegroup for the database to use. Is there a way to move existing tables there?
-- Mark McGibney, London, England
A: There are two issues here: One is the disk space issue, and the other relates to using filegroups. The two aren't the same thing. If all you want to do is increase available disk space for your database, you can do that without creating new filegroups. The real purpose of filegroups is to create logical relationships between multiple database files (likely on separate hard drives). You can administer these relationships together. All databases have at least one filegroup -- the primary filegroup -- which is also the default.
So to deal with your primary problem of getting more disk space for your database, you can create a new secondary data file on your hard drive (it'll have the extension .NDF, as opposed to the primary data file with the .MDF extension). When you create the new file, it automatically goes into the primary filegroup and is available for all tables to use.
Deliberately distributing tables across multiple drives is a pretty straightforward performance trick. Of course it only makes sense if you're using the table in such a way that it's likely to need multiple drives; you need to access different areas of the table simultaneously for there to be any benefit. Also you can get about the same benefit using a RAID array (whether 0, 1, or 5) without logically complicating your database. I'm prone to the RAID 5 solution myself; it's cost-effective, simple to operate, and provides extra data protection for the database, because you can have one hard drive fail and the system continues to function normally (albeit with a lot of beeping about the failed drive).
But suppose you don't want all tables distributed to all the database files? Perhaps one particular table (or tables) is the primary bottleneck of your application, and you want to focus on a solution for just that one part of the database. That's where filegroups come in. You can create a new filegroup, assign database files to it, then assign tables to it, and only the tables in that filegroup have access to your distributed database file structure.
It's easy to create a table in a specific filegroup. At the end of the CREATE TABLE statement, add an ON clause, specifying the filegroup, like this:
CREATE TABLE foo (mycol1 int) ON myFileGroup
But what if you have an existing table? The easiest trick I know to move a table from one filegroup to another is to create (or recreate) a clustered index on the table with the ON clause. A clustered index is the physical order of the table itself, unlike unclustered indexes, which are like their own little tables that contain only the columns you specify for the index plus a RID (row identifier). So when you create a clustered index on a new filegroup, it forces SQL Server to move the entire table to the new filegroup.
This is no more arduous than creating a clustered index on the default filegroup, but that doesn't trivialize it. When you create a clustered index, you're essentially rewriting the entire table in a new order. If there are many millions of rows, expect it to take awhile. And it's in your best interest to do a backup of the database before doing such serious operations.
As far as unclustered indexes go, you can improve performance by putting unclustered indexes in a separate filegroup from the actual table. That presumes the two filegroups don't share any hard drives (and preferably don't share any controllers either) and that your queries involve both the table and the index at the same time. In that case, because SQL Server can search both the index and table simultaneously using separate drives, it runs faster.
In SQL Server 2005 we get much smarter filegroups with the advent of partitioning schemes. In partitioning schemes, you can specify what parts of a table go into what filegroups. This lends a lot more control to using multiple drives across multiple filegroups, as well as being able to restrict what tables use multiple filegroups.
I've had situations where using multiple filegroups has worked out great, but you have to do your research first. Use SQL Profiler to study your database's behavior and lots of query analysis to show what the queries do. When you find a situation where the velocity and frequency is high and the query plan makes sense, you benefit greatly from using multiple filegroups.
But it can go the other way too. Using lots of separate database files and filegroups can create so many parallel disk threads that the cost of handling the threads outweighs the benefits of distributing data. Just be careful out there -- take your time and test thoroughly before going filegroup crazy. This is another reason why investing in more advanced hardware -- such as high-performance RAID controllers -- makes a lot of sense: there's very little downside to them and you still have the logical organizational options as well.
Q: We've been having problems with disk space on our SQL Server. I've been deleting old, unimportant data, but that isn't enough. I set up additional hard drive space on a separate drive, and I know how to create a new filegroup for the database to use. Is there a way to move existing tables there?
-- Mark McGibney, London, England
A: There are two issues here: One is the disk space issue, and the other relates to using filegroups. The two aren't the same thing. If all you want to do is increase available disk space for your database, you can do that without creating new filegroups. The real purpose of filegroups is to create logical relationships between multiple database files (likely on separate hard drives). You can administer these relationships together. All databases have at least one filegroup -- the primary filegroup -- which is also the default.
So to deal with your primary problem of getting more disk space for your database, you can create a new secondary data file on your hard drive (it'll have the extension .NDF, as opposed to the primary data file with the .MDF extension). When you create the new file, it automatically goes into the primary filegroup and is available for all tables to use.
Deliberately distributing tables across multiple drives is a pretty straightforward performance trick. Of course it only makes sense if you're using the table in such a way that it's likely to need multiple drives; you need to access different areas of the table simultaneously for there to be any benefit. Also you can get about the same benefit using a RAID array (whether 0, 1, or 5) without logically complicating your database. I'm prone to the RAID 5 solution myself; it's cost-effective, simple to operate, and provides extra data protection for the database, because you can have one hard drive fail and the system continues to function normally (albeit with a lot of beeping about the failed drive).
But suppose you don't want all tables distributed to all the database files? Perhaps one particular table (or tables) is the primary bottleneck of your application, and you want to focus on a solution for just that one part of the database. That's where filegroups come in. You can create a new filegroup, assign database files to it, then assign tables to it, and only the tables in that filegroup have access to your distributed database file structure.
It's easy to create a table in a specific filegroup. At the end of the CREATE TABLE statement, add an ON clause, specifying the filegroup, like this:
CREATE TABLE foo (mycol1 int) ON myFileGroup
But what if you have an existing table? The easiest trick I know to move a table from one filegroup to another is to create (or recreate) a clustered index on the table with the ON clause. A clustered index is the physical order of the table itself, unlike unclustered indexes, which are like their own little tables that contain only the columns you specify for the index plus a RID (row identifier). So when you create a clustered index on a new filegroup, it forces SQL Server to move the entire table to the new filegroup.
This is no more arduous than creating a clustered index on the default filegroup, but that doesn't trivialize it. When you create a clustered index, you're essentially rewriting the entire table in a new order. If there are many millions of rows, expect it to take awhile. And it's in your best interest to do a backup of the database before doing such serious operations.
As far as unclustered indexes go, you can improve performance by putting unclustered indexes in a separate filegroup from the actual table. That presumes the two filegroups don't share any hard drives (and preferably don't share any controllers either) and that your queries involve both the table and the index at the same time. In that case, because SQL Server can search both the index and table simultaneously using separate drives, it runs faster.
In SQL Server 2005 we get much smarter filegroups with the advent of partitioning schemes. In partitioning schemes, you can specify what parts of a table go into what filegroups. This lends a lot more control to using multiple drives across multiple filegroups, as well as being able to restrict what tables use multiple filegroups.
I've had situations where using multiple filegroups has worked out great, but you have to do your research first. Use SQL Profiler to study your database's behavior and lots of query analysis to show what the queries do. When you find a situation where the velocity and frequency is high and the query plan makes sense, you benefit greatly from using multiple filegroups.
But it can go the other way too. Using lots of separate database files and filegroups can create so many parallel disk threads that the cost of handling the threads outweighs the benefits of distributing data. Just be careful out there -- take your time and test thoroughly before going filegroup crazy. This is another reason why investing in more advanced hardware -- such as high-performance RAID controllers -- makes a lot of sense: there's very little downside to them and you still have the logical organizational options as well.
P2P alternative USENET resource
http://www.nzb-magic.com/forum/f7/?language=zh-CN
http://www.giganews.com/#
http://usenetreviews.info/astraweb
ref:
http://www.hdpop.cn/forum.php?mod=viewthread&tid=110&extra=page%3D64&ordertype=1
http://www.ruanyifeng.com/blog/2008/02/newsgroups_the_ultimate_p2p_alternative.html
http://gavinblog.blog.hexun.com/29566142_d.html
http://www.mr6.info/2009/02/p2p%E4%B8%8B%E8%BD%BD%E7%9A%84%E6%9B%BF%E4%BB%A3%E8%80%85-usenet/
http://www.giganews.com/#
http://usenetreviews.info/astraweb
ref:
http://www.hdpop.cn/forum.php?mod=viewthread&tid=110&extra=page%3D64&ordertype=1
http://www.ruanyifeng.com/blog/2008/02/newsgroups_the_ultimate_p2p_alternative.html
http://gavinblog.blog.hexun.com/29566142_d.html
http://www.mr6.info/2009/02/p2p%E4%B8%8B%E8%BD%BD%E7%9A%84%E6%9B%BF%E4%BB%A3%E8%80%85-usenet/
Wednesday, September 22, 2010
如何使用SQLDiag工具来追踪死锁错误(ZT)
SQLDiag最初是在SQL Server 7.0中引入的,它是一个非常方便的工具可以用来监控数据库服务器中出现的问题。这个命令行工具可以为微软的客户提供必需的信息,在运行 时,SQLDiag可以将不同的SQL Server工具提供的数据输出到一个文本文件中,以便于您阅览,该文本文件包含了配置、数据库和错误日志的信息。
在SQL Server 2005中,您可以将 SQLDiag作为一个服务运行,也可以将它作为一个命令行工具。在以下的讨论中,我将假定您的机器上运行的是非集群的SQL Server 2000,而我将通过命令行提示符来发出命令。[b] [/b]
[b]实战[/b][b]SQLDiag[/b]
我觉得实际操作比阅读更容易吸收技术信息,让我们通过一个实例来看看SQLDiag是如何工作的,以及怎样用它让数据库管理员的日子好过些。在这个例子中,我将展示如何捕获造成数据库服务器死锁的语句,并进行研究,然后使用一些技巧性的调整来避免死锁的出现。
如果您对死锁不太熟悉,也不了解它们是怎样对数据库系统造成严重破坏的,可以参考我以前的文章,我可以对死锁做一些简单的解释,以及如何在SQL Server 2005中捕获死锁并重试。
在 服务器上捕获死锁信息之前,我必需开启服务器上的一些追踪标记,一个追踪标记是设定在SQL Server 中的一种状态,它可以监测到服务器对非法操作的响应。在这种情况下,我要开启可以监测死锁错误的追踪标记,并在错误发生时将这些信息写入错误日志。为了开 启这些追踪标记,请执行以下的命令:(您必需具备SQL Server系统管理员权限来运行DBCC命令)
DBCC TRACEON(1204, -1)
DBCC TRACEON(1205, -1)
DBCC TRACEON(3605, -1)
1204 标记将返回死锁时遇到的锁的类型;1205标记则会返回更加详细的信息,它可以记录出现死锁时正在运行的语句;3605标记将把追踪信息发送到错误日 志,SQLDiag工具可以将这些信息输出到一个文本文件中。命令中的“-1”参数表示对所有的数据库连接应用追踪标记。
现在系统已经具备捕获死锁的能力了,现在让我们来创造一个死锁的情况,在列表A中,我创建了一些表格来制造死锁。
IF EXISTS(SELECT [name] FROM sysobjects WHERE type = 'U' AND name = 'DeadlockTable1')
DROP TABLE DeadlockTable1
GO
IF EXISTS(SELECT [name] FROM sysobjects WHERE type = 'U' AND name = 'DeadlockTable2')
DROP TABLE DeadlockTable2
GO
CREATE TABLE DeadlockTable1
(
IDCol TINYINT IDENTITY (1,1) PRIMARY KEY,
DeadlockValue1 VARCHAR(20)
)
GO
CREATE TABLE DeadlockTable2
(
IDCol TINYINT IDENTITY (1,1) PRIMARY KEY,
DeadlockValue2 VARCHAR(20)
)
GO
列表A
现在表格已经创建好了,我将在每个表格中插入一行,这样我们就有一个值来更新了,我将使用两条临近的更新语句来造成死锁,如列表B所示:
INSERT INTO DeadlockTable1 (DeadlockValue1)
SELECT 'Deadlock1'
INSERT INTO DeadlockTable2 (DeadlockValue2)
SELECT 'Deadlock2'
GO
列表B
这 部分很有意思,在以上的代码中,我在每一个表格中都添加了一行更新语句,但是这两条语句又都在互相争夺表资源,最终会造成死锁情况的发生。在此,我将使用 两个单独的数据库连接,剪切并粘贴这部分SQL Server代码到一个连接中,我将它命名为连接A,参见列表C,然后,剪切并粘贴这部分SQL Server代码到另外一个连接,我将它命名为连接B,参见列表D。
BEGIN TRANSACTION
UPDATE DeadlockTable2
SET DeadlockValue2 = 'Connection1'
WAITFOR DELAY '0:0:3'
UPDATE DeadlockTable1
SET DeadlockValue1 = 'Connection1'
COMMIT TRANSACTION
列表C
BEGIN TRANSACTION
UPDATE DeadlockTable1
SET DeadlockValue1 = 'Connection2'
WAITFOR DELAY '0:0:6'
UPDATE DeadlockTable2
SET DeadlockValue2 = 'Connection2'
COMMIT TRANSACTION
列表D
为 了制造死锁,您需要首先运行连接A中的代码,紧接着运行连接B中的代码,正如连接A中WAITFOR DELAY语句所示的那样,您大约有3秒钟的时间来切换连接并执行连接B中的代码。如果您正确执行了以上步骤,那将会在一个查询窗口中收到和下面这条信息 非常相似的出错信息:
Server: Msg 1205, Level 13, State 50, Line 1
Transaction (Process ID 53) was deadlocked on
resources with another process
and has been chosen as the deadlock victim. Rerun the transaction.
发 生死锁是因为两个连接之间发生了资源争夺,连接A锁定了DeadlockTable2并试图更新DeadlockTable1,而这是无法实现的,因为与 此同时,连接B锁定了DeadlockTable1,而且需要在DeadlockTable2上运行更新语句,这个场景是一个非常经典的例子,这也是为什 么在设计事务的时候,您要尽可能按照相同的使用顺序来更新表格,这一点非常重要。
如果您按照这种方式来设计事务,那么出现这种令人头疼的情况的可能性就会降低很多。SQL Server数据库引擎有专门的算法来通知您有这种情况出现,它还会系统性地关闭一个进程并允许另外一个顺利完成。
现 在我们已经体验了死锁,我们可以使用SQLDiag工具将错误信息输出到一个文本文件了。您可能会感到奇怪,既然在出现死锁错误的情况下可以从屏幕上看到 错误信息,为什么还要将这些信息输出到文本文件中呢?开启追踪标记可以捕获在您的系统上发生的所有死锁,这对于有大量数据更新的系统来说,这些信息是非常 有价值的。在文本文件中查找并观察何时发生错误、哪些对象牵连在错误中,可以节省您大量的研究时间。
为了执行SQLDiag工具,打开一个命令提示符窗口并浏览到SQL Server安装目录中的Binn文件夹。一个可能出现该工具的文件夹是C:Program FilesMicrosoft SQL ServerMSSQLBinn。
在使用这个工具的时候,您可能会用到一些参数,我会用到-E和-O开关,-E的含义是在执行是使用集成的安全属性;而-O开关可以指定您要输出的文件路径,以下是使用该工具参数的一个例子:
C:Program FilesMicrosoft SQL ServerMSSQLBinn
SQLDiag –E –O C:SQLDiagOutput.txt
[b]Conclusion[/b]
死 锁,尤其在2005版之前的SQL Server中,常常是数据库管理员的致命伤,如果没有好的方法来捕获并重现死锁事件,数据库管理员和开发者不得不依赖SQL Profiler和其它的工具来捕获死锁,并用于进一步的研究工作。SQLDiag是一个非常有效的追踪工具,不仅可以用来对付这些令人尴尬的死锁错误, 还可以用来捕获SQL Server环境中很多其它的诊断信息。我建议您要花些时间来研究这个强大的工具,而不仅仅是尝试本文中的例子,因为SQLDiag可以作为预防性的工具 来避免未来可能出现的令人头痛的问题。
在SQL Server 2005中,您可以将 SQLDiag作为一个服务运行,也可以将它作为一个命令行工具。在以下的讨论中,我将假定您的机器上运行的是非集群的SQL Server 2000,而我将通过命令行提示符来发出命令。[b] [/b]
[b]实战[/b][b]SQLDiag[/b]
我觉得实际操作比阅读更容易吸收技术信息,让我们通过一个实例来看看SQLDiag是如何工作的,以及怎样用它让数据库管理员的日子好过些。在这个例子中,我将展示如何捕获造成数据库服务器死锁的语句,并进行研究,然后使用一些技巧性的调整来避免死锁的出现。
如果您对死锁不太熟悉,也不了解它们是怎样对数据库系统造成严重破坏的,可以参考我以前的文章,我可以对死锁做一些简单的解释,以及如何在SQL Server 2005中捕获死锁并重试。
在 服务器上捕获死锁信息之前,我必需开启服务器上的一些追踪标记,一个追踪标记是设定在SQL Server 中的一种状态,它可以监测到服务器对非法操作的响应。在这种情况下,我要开启可以监测死锁错误的追踪标记,并在错误发生时将这些信息写入错误日志。为了开 启这些追踪标记,请执行以下的命令:(您必需具备SQL Server系统管理员权限来运行DBCC命令)
DBCC TRACEON(1204, -1)
DBCC TRACEON(1205, -1)
DBCC TRACEON(3605, -1)
1204 标记将返回死锁时遇到的锁的类型;1205标记则会返回更加详细的信息,它可以记录出现死锁时正在运行的语句;3605标记将把追踪信息发送到错误日 志,SQLDiag工具可以将这些信息输出到一个文本文件中。命令中的“-1”参数表示对所有的数据库连接应用追踪标记。
现在系统已经具备捕获死锁的能力了,现在让我们来创造一个死锁的情况,在列表A中,我创建了一些表格来制造死锁。
IF EXISTS(SELECT [name] FROM sysobjects WHERE type = 'U' AND name = 'DeadlockTable1')
DROP TABLE DeadlockTable1
GO
IF EXISTS(SELECT [name] FROM sysobjects WHERE type = 'U' AND name = 'DeadlockTable2')
DROP TABLE DeadlockTable2
GO
CREATE TABLE DeadlockTable1
(
IDCol TINYINT IDENTITY (1,1) PRIMARY KEY,
DeadlockValue1 VARCHAR(20)
)
GO
CREATE TABLE DeadlockTable2
(
IDCol TINYINT IDENTITY (1,1) PRIMARY KEY,
DeadlockValue2 VARCHAR(20)
)
GO
列表A
现在表格已经创建好了,我将在每个表格中插入一行,这样我们就有一个值来更新了,我将使用两条临近的更新语句来造成死锁,如列表B所示:
INSERT INTO DeadlockTable1 (DeadlockValue1)
SELECT 'Deadlock1'
INSERT INTO DeadlockTable2 (DeadlockValue2)
SELECT 'Deadlock2'
GO
列表B
这 部分很有意思,在以上的代码中,我在每一个表格中都添加了一行更新语句,但是这两条语句又都在互相争夺表资源,最终会造成死锁情况的发生。在此,我将使用 两个单独的数据库连接,剪切并粘贴这部分SQL Server代码到一个连接中,我将它命名为连接A,参见列表C,然后,剪切并粘贴这部分SQL Server代码到另外一个连接,我将它命名为连接B,参见列表D。
BEGIN TRANSACTION
UPDATE DeadlockTable2
SET DeadlockValue2 = 'Connection1'
WAITFOR DELAY '0:0:3'
UPDATE DeadlockTable1
SET DeadlockValue1 = 'Connection1'
COMMIT TRANSACTION
列表C
BEGIN TRANSACTION
UPDATE DeadlockTable1
SET DeadlockValue1 = 'Connection2'
WAITFOR DELAY '0:0:6'
UPDATE DeadlockTable2
SET DeadlockValue2 = 'Connection2'
COMMIT TRANSACTION
列表D
为 了制造死锁,您需要首先运行连接A中的代码,紧接着运行连接B中的代码,正如连接A中WAITFOR DELAY语句所示的那样,您大约有3秒钟的时间来切换连接并执行连接B中的代码。如果您正确执行了以上步骤,那将会在一个查询窗口中收到和下面这条信息 非常相似的出错信息:
Server: Msg 1205, Level 13, State 50, Line 1
Transaction (Process ID 53) was deadlocked on
resources with another process
and has been chosen as the deadlock victim. Rerun the transaction.
发 生死锁是因为两个连接之间发生了资源争夺,连接A锁定了DeadlockTable2并试图更新DeadlockTable1,而这是无法实现的,因为与 此同时,连接B锁定了DeadlockTable1,而且需要在DeadlockTable2上运行更新语句,这个场景是一个非常经典的例子,这也是为什 么在设计事务的时候,您要尽可能按照相同的使用顺序来更新表格,这一点非常重要。
如果您按照这种方式来设计事务,那么出现这种令人头疼的情况的可能性就会降低很多。SQL Server数据库引擎有专门的算法来通知您有这种情况出现,它还会系统性地关闭一个进程并允许另外一个顺利完成。
现 在我们已经体验了死锁,我们可以使用SQLDiag工具将错误信息输出到一个文本文件了。您可能会感到奇怪,既然在出现死锁错误的情况下可以从屏幕上看到 错误信息,为什么还要将这些信息输出到文本文件中呢?开启追踪标记可以捕获在您的系统上发生的所有死锁,这对于有大量数据更新的系统来说,这些信息是非常 有价值的。在文本文件中查找并观察何时发生错误、哪些对象牵连在错误中,可以节省您大量的研究时间。
为了执行SQLDiag工具,打开一个命令提示符窗口并浏览到SQL Server安装目录中的Binn文件夹。一个可能出现该工具的文件夹是C:Program FilesMicrosoft SQL ServerMSSQLBinn。
在使用这个工具的时候,您可能会用到一些参数,我会用到-E和-O开关,-E的含义是在执行是使用集成的安全属性;而-O开关可以指定您要输出的文件路径,以下是使用该工具参数的一个例子:
C:Program FilesMicrosoft SQL ServerMSSQLBinn
SQLDiag –E –O C:SQLDiagOutput.txt
[b]Conclusion[/b]
死 锁,尤其在2005版之前的SQL Server中,常常是数据库管理员的致命伤,如果没有好的方法来捕获并重现死锁事件,数据库管理员和开发者不得不依赖SQL Profiler和其它的工具来捕获死锁,并用于进一步的研究工作。SQLDiag是一个非常有效的追踪工具,不仅可以用来对付这些令人尴尬的死锁错误, 还可以用来捕获SQL Server环境中很多其它的诊断信息。我建议您要花些时间来研究这个强大的工具,而不仅仅是尝试本文中的例子,因为SQLDiag可以作为预防性的工具 来避免未来可能出现的令人头痛的问题。
解决/优化SQL Server查询速度慢的方法
1、把数据、日志、索引放到不同的I/O设备上,增加读取速度,以前可以将Tempdb应放在RAID0上,SQL2000不在支持。数据量(尺寸)越大,提高I/O越重要。
2、纵向、横向分割表,减少表的尺寸(sp_spaceuse)
3、升级硬件
4、根据SQL Server查询条件,建立索引,优化索引、优化访问方式,限制结果集的数据量。注意填充因子要适当(最好是使用默认值0)。索引应该尽量小,使用字节数小的列建索引好(参照索引的创建),不要对有限的几个值的字段建单一索引如性别字段。
5、提高网速。
6、扩大服务器的内存,Windows 2000和SQL server 2000能支持4-8G的内存。
配置虚拟内存:虚拟内存大小应基于计算机上并发运行的服务进行配置。运行 Microsoft SQL Server? 2000时,可考虑将虚拟内存大小设置为计算机中安装的物理内存的1.5倍。如果另外安装了全文检索功能,并打算运行Microsoft搜索服务以便执行 全文索引和SQL Server查询。
可考虑:将虚拟内存大小配置为至少是计算机中安装的物理内存的3倍。将SQL Server max server memory服务器配置选项配置为物理内存的1.5倍(虚拟内存大小设置的一半)。
7、增加服务器CPU个数;但是必须 明白并行处理串行处理更需要资源例如内存。使用并行还是串行程是MsSQL自动评估选择的。单个任务分解成多个任务,就可以在处理器上运行。例如耽搁查询 的排序、连接、扫描和GROUP BY字句同时执行,SQL SERVER根据系统的负载情况决定最优的并行等级,复杂的需要消耗大量的CPU的查询最适合并行处理。但是更新操作UPDATE,INSERT, DELETE还不能并行处理。
8、如果是使用like进行查询的话,简单的使用index是不行的,但是全文索引,耗空间。 like ''a%'' 使用索引 like ''%a'' 不使用索引用 like ''%a%'' 查询时,SQL Server查询耗时和字段值总长度成正比,所以不能用CHAR类型,而是VARCHAR。对于字段的值很长的建全文索引。
9、DB Server 和APPLication Server 分离;OLTP和OLAP分离
10、分布式分区视图可用于实现数据库服务器联合体。
联合体是一组分开管理的服务器,但它们相互协作分担系统的处理负荷。这种通过分区数据形成数据库服务器联合体的机制能够扩大一组服务器,以支持大型的多层 Web 站点的处理需要。有关更多信息,参见设计联合数据库服务器。(参照SQL帮助文件''分区视图'')
a、在实现分区视图之前,必须先水平分区表
b、 在创建成员表后,在每个成员服务器上定义一个分布式分区视图,并且每个视图具有相同的名称。这样,引用分布式分区视图名的查询可以在任何一个成员服务器上 运行。系统操作如同每个成员服务器上都有一个原始表的复本一样,但其实每个服务器上只有一个成员表和一个分布式分区视图。数据的位置对应用程序是透明的。
11、重建索引 DBCC REINDEX ,DBCC INDEXDEFRAG,收缩数据和日志 DBCC SHRINKDB,DBCC SHRINKFILE. 设置自动收缩日志.对于大的数据库不要设置数据库自动增长,它会降低服务器的性能。
在T-sql的写法上有很大的讲究,下面列出常见的要点:首先,DBMS处理SQL Server查询计划的过程是这样的:
1、 查询语句的词法、语法检查
2、 将语句提交给DBMS的查询优化器
3、 优化器做代数优化和存取路径的优化
4、 由预编译模块生成SQL Server查询规划
5、 然后在合适的时间提交给系统处理执行
6、 最后将执行结果返回给用户。
其次,看一下SQL SERVER的数据存放的结构:一个页面的大小为8K(8060)字节,8个页面为一个盘区,按照B树存放。
12、 Commit和rollback的区别 Rollback:回滚所有的事物。 Commit:提交当前的事物. 没有必要在动态SQL里写事物,如果要写请写在外面如: begin tran exec(@s) commit trans 或者将动态SQL 写成函数或者存储过程。
13、在查询Select语句中用Where字句限制返回的行数,避免表扫描,如果返回不必要的数据,浪费了服务器的I/O资源,加重了网络的负担降低性能。如果表很大,在表扫描的期间将表锁住,禁止其他的联接访问表,后果严重。
14、SQL的注释申明对执行没有任何影响
分析方法:
第一、先优化一下索引,索引对数据查询速度影响很大的。
第二、将日志文件与数据文件分开存放。
第三、优化系统中存储过程的查询条件,这个是提高查询速度的最基本,曾在一个大型公司的数据库中写存储过程,取数是从北京,上海,广州三地取数,数据量超过50万,整个查询不超过 10秒。就是因为索引与存储过程的优化。
–首先从两个方面:
1\分析是硬件的问题,比如内存经常在90%,CPU经常在80%以上,建议加硬件了.提升硬件速度.加内存,内存够的话对整个磁盘的读写能力会减轻很多.我们公司以前的内存是4G,现在升级为64位,可以用16G,速度大幅度提高,但有时也会出现慢,只是有时锁的问题…
硬盘建议用RAID0+1,现在的硬盘又不贵.数据库一般都建议用RAID10.一是安全,二是速度.都比较有保障.
2\软件方面:
检测耗用内存,CPU最多的语句或过程,进行跟踪优化,SQL2005中有一个表sys.dm_exec_query_stats可以看到.当然也可以根据Read80Trace程序进行统计跟踪.(比如一个小时的跟踪查看耗用资源最多的语句).
根据这些信息再来优化数据,如:加索引,分区表,….优化语句啊.
总结:以前听过一句话, 数据库慢的80%的因素是SQL语句.所以把SQL语句优化好对速度提高很快的当然加硬件也可以的
1、把系统换成64位,然后加大内存。
2、数据库性能的优化。相信很多查询都是有很大的优化空间的,也不清楚你们有没有专门的数据库维护人员,看一下索引碎片之类的情况。
2、纵向、横向分割表,减少表的尺寸(sp_spaceuse)
3、升级硬件
4、根据SQL Server查询条件,建立索引,优化索引、优化访问方式,限制结果集的数据量。注意填充因子要适当(最好是使用默认值0)。索引应该尽量小,使用字节数小的列建索引好(参照索引的创建),不要对有限的几个值的字段建单一索引如性别字段。
5、提高网速。
6、扩大服务器的内存,Windows 2000和SQL server 2000能支持4-8G的内存。
配置虚拟内存:虚拟内存大小应基于计算机上并发运行的服务进行配置。运行 Microsoft SQL Server? 2000时,可考虑将虚拟内存大小设置为计算机中安装的物理内存的1.5倍。如果另外安装了全文检索功能,并打算运行Microsoft搜索服务以便执行 全文索引和SQL Server查询。
可考虑:将虚拟内存大小配置为至少是计算机中安装的物理内存的3倍。将SQL Server max server memory服务器配置选项配置为物理内存的1.5倍(虚拟内存大小设置的一半)。
7、增加服务器CPU个数;但是必须 明白并行处理串行处理更需要资源例如内存。使用并行还是串行程是MsSQL自动评估选择的。单个任务分解成多个任务,就可以在处理器上运行。例如耽搁查询 的排序、连接、扫描和GROUP BY字句同时执行,SQL SERVER根据系统的负载情况决定最优的并行等级,复杂的需要消耗大量的CPU的查询最适合并行处理。但是更新操作UPDATE,INSERT, DELETE还不能并行处理。
8、如果是使用like进行查询的话,简单的使用index是不行的,但是全文索引,耗空间。 like ''a%'' 使用索引 like ''%a'' 不使用索引用 like ''%a%'' 查询时,SQL Server查询耗时和字段值总长度成正比,所以不能用CHAR类型,而是VARCHAR。对于字段的值很长的建全文索引。
9、DB Server 和APPLication Server 分离;OLTP和OLAP分离
10、分布式分区视图可用于实现数据库服务器联合体。
联合体是一组分开管理的服务器,但它们相互协作分担系统的处理负荷。这种通过分区数据形成数据库服务器联合体的机制能够扩大一组服务器,以支持大型的多层 Web 站点的处理需要。有关更多信息,参见设计联合数据库服务器。(参照SQL帮助文件''分区视图'')
a、在实现分区视图之前,必须先水平分区表
b、 在创建成员表后,在每个成员服务器上定义一个分布式分区视图,并且每个视图具有相同的名称。这样,引用分布式分区视图名的查询可以在任何一个成员服务器上 运行。系统操作如同每个成员服务器上都有一个原始表的复本一样,但其实每个服务器上只有一个成员表和一个分布式分区视图。数据的位置对应用程序是透明的。
11、重建索引 DBCC REINDEX ,DBCC INDEXDEFRAG,收缩数据和日志 DBCC SHRINKDB,DBCC SHRINKFILE. 设置自动收缩日志.对于大的数据库不要设置数据库自动增长,它会降低服务器的性能。
在T-sql的写法上有很大的讲究,下面列出常见的要点:首先,DBMS处理SQL Server查询计划的过程是这样的:
1、 查询语句的词法、语法检查
2、 将语句提交给DBMS的查询优化器
3、 优化器做代数优化和存取路径的优化
4、 由预编译模块生成SQL Server查询规划
5、 然后在合适的时间提交给系统处理执行
6、 最后将执行结果返回给用户。
其次,看一下SQL SERVER的数据存放的结构:一个页面的大小为8K(8060)字节,8个页面为一个盘区,按照B树存放。
12、 Commit和rollback的区别 Rollback:回滚所有的事物。 Commit:提交当前的事物. 没有必要在动态SQL里写事物,如果要写请写在外面如: begin tran exec(@s) commit trans 或者将动态SQL 写成函数或者存储过程。
13、在查询Select语句中用Where字句限制返回的行数,避免表扫描,如果返回不必要的数据,浪费了服务器的I/O资源,加重了网络的负担降低性能。如果表很大,在表扫描的期间将表锁住,禁止其他的联接访问表,后果严重。
14、SQL的注释申明对执行没有任何影响
分析方法:
第一、先优化一下索引,索引对数据查询速度影响很大的。
第二、将日志文件与数据文件分开存放。
第三、优化系统中存储过程的查询条件,这个是提高查询速度的最基本,曾在一个大型公司的数据库中写存储过程,取数是从北京,上海,广州三地取数,数据量超过50万,整个查询不超过 10秒。就是因为索引与存储过程的优化。
–首先从两个方面:
1\分析是硬件的问题,比如内存经常在90%,CPU经常在80%以上,建议加硬件了.提升硬件速度.加内存,内存够的话对整个磁盘的读写能力会减轻很多.我们公司以前的内存是4G,现在升级为64位,可以用16G,速度大幅度提高,但有时也会出现慢,只是有时锁的问题…
硬盘建议用RAID0+1,现在的硬盘又不贵.数据库一般都建议用RAID10.一是安全,二是速度.都比较有保障.
2\软件方面:
检测耗用内存,CPU最多的语句或过程,进行跟踪优化,SQL2005中有一个表sys.dm_exec_query_stats可以看到.当然也可以根据Read80Trace程序进行统计跟踪.(比如一个小时的跟踪查看耗用资源最多的语句).
根据这些信息再来优化数据,如:加索引,分区表,….优化语句啊.
总结:以前听过一句话, 数据库慢的80%的因素是SQL语句.所以把SQL语句优化好对速度提高很快的当然加硬件也可以的
A. 按平均 CPU 时间排在前五个的查询 此方案提供有关 CPU 时间、IO 读写以及按平均 CPU 时间排在前五个查询的执行次数的信息。SELECT TOP 5 total_worker_time/execution_count AS [Avg CPU Time],
(SELECT SUBSTRING(text,statement_start_offset/2,(CASE WHEN statement_end_offset = -1 then LEN(CONVERT(nvarchar(max), text)) * 2 ELSE statement_end_offset end -statement_start_offset)/2) FROM sys.dm_exec_sql_text(sql_handle)) AS query_textFROM sys.dm_exec_query_statsORDER BY [Avg CPU Time] DESC
还是建议做个SQLDIAG的诊断报告,获得整个系统的性能信息,然后才能更有针对性的做出调整。
1、把系统换成64位,然后加大内存。
2、数据库性能的优化。相信很多查询都是有很大的优化空间的,也不清楚你们有没有专门的数据库维护人员,看一下索引碎片之类的情况。
Important: ASP.NET Security Vulnerability
http://weblogs.asp.net/scottgu/archive/2010/09/18/important-asp-net-security-vulnerability.aspx
Tuesday, September 21, 2010
Win2008/ R2 IIS7.x Classic Asp upload 200K limit solution
During the process of migrating a site to IIS 7 we came across an issue with Classic ASP file uploads throwing 500 errors when larger than 200kb. There is an EASY fix for this.
In IIS 7, click your site and expand it then click the ASP icon.
Expand the Limits Properties icon, and change the value in the “Maximum Requesting Entity Body Limit” to a value larger than 200000 (which is about 200kb). 2000000 would be roughly 2mb, 20000000 would be 20mb.
Click the APPLY button. That’s it!
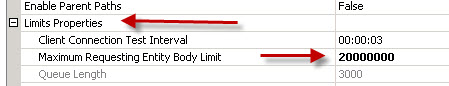
In IIS 7, click your site and expand it then click the ASP icon.
Expand the Limits Properties icon, and change the value in the “Maximum Requesting Entity Body Limit” to a value larger than 200000 (which is about 200kb). 2000000 would be roughly 2mb, 20000000 would be 20mb.
Click the APPLY button. That’s it!

IIS7.0的修改方法如下:
打开IIS管理器--双击“IIS”中的“ASP”-- 打开“配置 ASP 应该程序的属性”--展开“限制属性”;
修改“最大请求实体主体限制”的值,默认值为200000(即不到200KB);
把它修改为你想修改的大小,如:52000000(50MB)。
修改完成点击“应用”OK!
IIS6.0的修改方法如下:
在服务里关闭iis admin service服务
找到windows\system32\inetsrv\下的metabase.xml,
打开,找到aspmaxrequestentityallowed 把他修改为需要的值,默认为204800,即200k
把它修改为51200000(50MB)
然后重启iis admin service服务
Tips for Classic ASP developers on IIS7.x
There are a few changes in IIS7 which Classic ASP developers should be aware of.
--------------------------------------------------------------------------------------------------------------------
HTTP Error 404.3 - Not Found
Description: The page you are requesting cannot be served because of the Multipurpose Internet Mail Extensions (MIME) map policy that is configured on the Web server. The page you requested has a file name extension that is not recognized, and is not allowed.
--------------------------------------------------------------------------------------------------------------------
Microsoft JET Database Engine error '80004005'
Unspecified error
This appcmd command will turn off loadUserProfile for the Default Application Pool. if your application runs in a different AppPool, make the corresponding change:
%windir%\system32\inetsrv\appcmd set config /section:applicationPools /[name='DefaultAppPool'].processModel.loadUserProfile:false
This command will ACL the Network Service temp directory to allow creator write / read privledges. If you run your Application Pool under a different identity, you'll need to ACL that owner's temp directory:
icacls %windir%\serviceprofiles\networkservice\AppData\Local\Temp /grant Users:(CI)(S,WD,AD,X)
icacls %windir%\serviceprofiles\networkservice\AppData\Local\Temp /grant "CREATOR OWNER":(OI)(CI)(IO)(F)
--------------------------------------------------------------------------------------------------------------------
An error occurred on the server when processing the URL. Please contact the system administrator
--------------------------------------------------------------------------------------------------------------------
To revert back to IIS6- behavior, simply run the following command:
%windir%\system32\inetsrv\appcmd set config -section:asp -scriptErrorSentToBrowser:true
Or you can find it in the UI here:
then you'll be back to seeing this style of error instead:
--------------------------------------------------------------------------------------------------------------------
Microsoft VBScript compilation error '800a03ea'
Syntax error
/test.asp, line 4
--------------------------------------------------------------------------------------------------------------------
Active Server Pages error 'ASP 0131'
Disallowed Parent Path
/test.asp, line 1
The Include file '../bad.inc' cannot contain '..' to indicate the parent directory.
--------------------------------------------------------------------------------------------------------------------
Server.MapPath() error 'ASP 0175 : 80004005'
Disallowed Path Characters
/testdir/test.asp, line 9
The '..' characters are not allowed in the Path parameter for the MapPath method.
--------------------------------------------------------------------------------------------------------------------
To revert back to IIS 5.x behavior, simply run the following command:
%windir%\system32\inetsrv\appcmd set config -section:asp -enableParentPaths:true
or you can find the UI setting here:
ASP not installed by default
First things first! If you're moving from XP to Windows Vista / Longhorn Server, you may be getting this error:--------------------------------------------------------------------------------------------------------------------
HTTP Error 404.3 - Not Found
Description: The page you are requesting cannot be served because of the Multipurpose Internet Mail Extensions (MIME) map policy that is configured on the Web server. The page you requested has a file name extension that is not recognized, and is not allowed.
--------------------------------------------------------------------------------------------------------------------
this is usually the case when you haven't installed the ASP component. Go to where you installed IIS and look under IIS/WWW Services/Application Development/ASP and install it. :)Access and Classic ASP
A lot of people use Access as a database - because it is small, can be copied around, and is easy to manage. One of the changes we made in IIS7 in Vista broke using ASP and Access by default. I described this change in more detail in this post, but essentially it has to do with the fact that Application Pools now use the Application Pool identity's profile and temporary directory, rather than \windows\temp by default. And since the only one that can write to Network Service's temp directory is the Network Service, anonymous or authenticated ASP applications break, since ASP uses the impersonated identity to access the database. If you use ASP and Access on IIS7, you've probably seen this error, or a variation of it:--------------------------------------------------------------------------------------------------------------------
Microsoft JET Database Engine error '80004005'
Unspecified error
--------------------------------------------------------------------------------------------------------------------
The answer is pretty straight forward: turn off loadUserProfile, or ACL the temp directory to allow writes. As a result of this and other compatibility issues, we're considering reverting this change in Longhorn Server / Vista SP1. In the mean time, you can work around it by doing either of the following:This appcmd command will turn off loadUserProfile for the Default Application Pool. if your application runs in a different AppPool, make the corresponding change:
%windir%\system32\inetsrv\appcmd set config /section:applicationPools /[name='DefaultAppPool'].processModel.loadUserProfile:false
This command will ACL the Network Service temp directory to allow creator write / read privledges. If you run your Application Pool under a different identity, you'll need to ACL that owner's temp directory:
icacls %windir%\serviceprofiles\networkservice\AppData\Local\Temp /grant Users:(CI)(S,WD,AD,X)
icacls %windir%\serviceprofiles\networkservice\AppData\Local\Temp /grant "CREATOR OWNER":(OI)(CI)(IO)(F)
**Update 2/19/2009** if you are having issues with Access and ASP you might want to read this terrific guide recently posted on IIS.NET: http://learn.iis.net/page.aspx/563/using-classic-asp-with-microsoft-access-databases-on-iis-70-and-iis-75/
Script errors no longer shown in browser by default
As a result of our security paranoia, we turned off ASP's default behavior of sending script errors (including line number and code snippet to the browser. So instead of seeing the typical error you would see ASP throw, you will now see this:--------------------------------------------------------------------------------------------------------------------
An error occurred on the server when processing the URL. Please contact the system administrator
--------------------------------------------------------------------------------------------------------------------
To revert back to IIS6- behavior, simply run the following command:
%windir%\system32\inetsrv\appcmd set config -section:asp -scriptErrorSentToBrowser:true
Or you can find it in the UI here:
then you'll be back to seeing this style of error instead:
--------------------------------------------------------------------------------------------------------------------
Microsoft VBScript compilation error '800a03ea'
Syntax error
/test.asp, line 4
Response.Write("I love classic ASP" && foo)
-------------------------------------^--------------------------------------------------------------------------------------------------------------------Parents paths disabled by default (redux)
We disabled parent paths by default with IIS6, but I've seen this hit people on Vista coming from XP, where it is still enabled by default in IIS5.1 The enableParentPaths setting determines where ASP "includes" should be allowed to escape the parent directory (eg. ../../../includeFile.inc). You'll see this error by default if you try to escape the current directory:--------------------------------------------------------------------------------------------------------------------
Active Server Pages error 'ASP 0131'
Disallowed Parent Path
/test.asp, line 1
The Include file '../bad.inc' cannot contain '..' to indicate the parent directory.
--------------------------------------------------------------------------------------------------------------------
or you may see this error if you are using a path with ../ in it and your ADODB code
--------------------------------------------------------------------------------------------------------------------Server.MapPath() error 'ASP 0175 : 80004005'
Disallowed Path Characters
/testdir/test.asp, line 9
The '..' characters are not allowed in the Path parameter for the MapPath method.
--------------------------------------------------------------------------------------------------------------------
To revert back to IIS 5.x behavior, simply run the following command:
%windir%\system32\inetsrv\appcmd set config -section:asp -enableParentPaths:true
or you can find the UI setting here:
APPL_PHYSICAL_PATH no longer returns "\" with path
If you use Request.ServerVariables("APPL_PHYSICAL_PATH") to get at the physical path for your application, you may notice that the physical path no longer returns with a trailing slash. In previous releases of IIS, we returned this value as stored in the metabase. In IIS7, we calculate this value based on the configuration store, and we never return a trailing slash. You'll need to account for this especially if you are the return value with some other part of the path in your application.Session_OnEnd not firing
If you find that Session_onEnd event in your global.asa is not firing, check out this blog post from Lou on the issue and the fix.Classic ASP on IIS 7 (setting, tips...)
It's not really difficult to run classic ASP on Internet Information Server 7, but there are some bumps down the road. Here's a little help to get you started:
First of all, check whether you have the Windows feature for ASP installed. Go to Programs and Features in Control Panel and click Turn Windows features on and off. Navigate down the tree of features and make sure ASP is checked.

Next, go to Internet Information Server (IIS) Manager (run inetmgr from the Start Search box to get there fast) and create a new application pool for ASP.

This should be a "No managed code" and "Classic" app pool if you do not intend to mix and match the .NET Framework and ASP.NET in the same pool. The Integrated pipeline would not make sense, because it only applies to integrating HTTP modules that are either native or managed .NET implementations.
I had some difficulties setting the identity of the application pool to the new built-in IUSR account. This account replaces the former computer account called IUSR_machinename. Same goes for the IIS_WPG group for application pools that is replaced by the builtin group IIS_IUSRS. Read more about it here. Under the Advanced Settings of the "ASP" application pool you will find the Identity property under Process Model. The default value is NetworkService. I found no way to set this to the BUILTIN\IUSR by choosing SpecificUser and setting BUILTIN\USR under Identity SpecificUser Credentials. I guess that you shouldn't be running ASP sites under IUSR anymore. It is used for anonymous users automatically.

To easy the administration effort, there is a way to turn off the IUSR account without turning off anonymous identification:
appcmd set config -section:anonymousAuthentication -userName:"" --password
And lastly, create your new web application. For example, copy the ASP site folder under C:\inetpub\wwwroot, where the default installation location of "Default Web Site" of IIS. Convert the folder (or virtual directory) to an application and choose "ASP" as the application pool. Check whether the .asp extension is mapped to the correct handler and whether it is enabled. Also make sure that the identity of your application pool has sufficient rights (and no more than that) to access the files in the web site's folder.

One final note: whenever there is a error in the ASP website, and you get this error message: "An error occurred on the server when processing the URL. Please contact the system administrator",

it's probably because by default no error messages are sent to the client in IIS7. Change the setting "Send Errors To Browser" of your web application under the ASP icon to reveal such errors.

Side note: if you get the nice Internet Explorer 500 error message and no particular details at all, remember to uncheck the "Show friendly HTTP error messages" checkbox under Internet Options, Advanced of IE.
First of all, check whether you have the Windows feature for ASP installed. Go to Programs and Features in Control Panel and click Turn Windows features on and off. Navigate down the tree of features and make sure ASP is checked.

Next, go to Internet Information Server (IIS) Manager (run inetmgr from the Start Search box to get there fast) and create a new application pool for ASP.

This should be a "No managed code" and "Classic" app pool if you do not intend to mix and match the .NET Framework and ASP.NET in the same pool. The Integrated pipeline would not make sense, because it only applies to integrating HTTP modules that are either native or managed .NET implementations.
I had some difficulties setting the identity of the application pool to the new built-in IUSR account. This account replaces the former computer account called IUSR_machinename. Same goes for the IIS_WPG group for application pools that is replaced by the builtin group IIS_IUSRS. Read more about it here. Under the Advanced Settings of the "ASP" application pool you will find the Identity property under Process Model. The default value is NetworkService. I found no way to set this to the BUILTIN\IUSR by choosing SpecificUser and setting BUILTIN\USR under Identity SpecificUser Credentials. I guess that you shouldn't be running ASP sites under IUSR anymore. It is used for anonymous users automatically.

To easy the administration effort, there is a way to turn off the IUSR account without turning off anonymous identification:
appcmd set config -section:anonymousAuthentication -userName:"" --password
And lastly, create your new web application. For example, copy the ASP site folder under C:\inetpub\wwwroot, where the default installation location of "Default Web Site" of IIS. Convert the folder (or virtual directory) to an application and choose "ASP" as the application pool. Check whether the .asp extension is mapped to the correct handler and whether it is enabled. Also make sure that the identity of your application pool has sufficient rights (and no more than that) to access the files in the web site's folder.

One final note: whenever there is a error in the ASP website, and you get this error message: "An error occurred on the server when processing the URL. Please contact the system administrator",

it's probably because by default no error messages are sent to the client in IIS7. Change the setting "Send Errors To Browser" of your web application under the ASP icon to reveal such errors.

Side note: if you get the nice Internet Explorer 500 error message and no particular details at all, remember to uncheck the "Show friendly HTTP error messages" checkbox under Internet Options, Advanced of IE.
Best Max Memory Settings for SQL Server 2005/2008
It is pretty important to make sure you set the Max Server memory setting for SQL Server 2005/2008 to something besides the default setting (which allows SQL Server to use as much memory as it wants, subject to signals from the operating system that it is under memory pressure). This is especially important with larger, busier systems that may be under memory pressure.
This setting controls how much memory can be used by the SQL Server Buffer Pool. If you don’t set an upper limit for this value, other parts of SQL Server, and the operating system can be starved for memory, which can cause instability and performance problems. It is even more important to set this correctly if you have “Lock Pages in Memory” enabled for the SQL Server service account (which I always do for x64 systems with more than 4GB of memory).
These settings are for x64, on a dedicated database server, only running the DB engine, (which is the ideal situation).
Physical RAM MaxServerMem Setting
2GB 1500
4GB 3200
6GB 4800
8GB 6400
12GB 10000
16GB 13500
24GB 21500
32GB 29000
48GB 44000
64GB 60000
72GB 68000
96GB 92000
128GB 124000
If you are running other SQL Server components, such as SSIS or Full Text Search, you will want to allocate less memory for the SQL Server Buffer Pool. You also want to pay close attention to how much memory is still available in Task Manager. This is how much RAM should be available in Task Manager while you are under load (on Windows Server 2003):
Physical RAM Target Avail RAM in Task Manager
< 4GB 512MB – 1GB
4-32GB 1GB – 2GB
32-128GB 2GB – 4GB
> 128GB > 4GB
You can use T-SQL to set your MaxServerMemory setting. The sample below sets it to 3500, which is the equivalent of 3.5GB. This setting is dynamic in SQL Server 2005/2008, which means that you can change it and it goes into effect immediately, without restarting SQL Server.
-- Turn on advanced optionsEXEC sp_configure'Show Advanced Options',1;GO
RECONFIGURE;GO
-- Set max server memory = 3500MB for the serverEXEC sp_configure'max server memory (MB)',3500;GO
RECONFIGURE;GO

Finally, I have learned that it is a good idea to temporarily adjust your MaxServerMemory setting downward by a few GB if you know you will be doing a large file copy on your database server (such as copying a large database backup file).
http://www.sqlservercentral.com/blogs/glennberry/archive/2009/10/29/suggested-max-memory-settings-for-sql-server-2005_2F00_2008.aspx
This setting controls how much memory can be used by the SQL Server Buffer Pool. If you don’t set an upper limit for this value, other parts of SQL Server, and the operating system can be starved for memory, which can cause instability and performance problems. It is even more important to set this correctly if you have “Lock Pages in Memory” enabled for the SQL Server service account (which I always do for x64 systems with more than 4GB of memory).
These settings are for x64, on a dedicated database server, only running the DB engine, (which is the ideal situation).
Physical RAM MaxServerMem Setting
2GB 1500
4GB 3200
6GB 4800
8GB 6400
12GB 10000
16GB 13500
24GB 21500
32GB 29000
48GB 44000
64GB 60000
72GB 68000
96GB 92000
128GB 124000
If you are running other SQL Server components, such as SSIS or Full Text Search, you will want to allocate less memory for the SQL Server Buffer Pool. You also want to pay close attention to how much memory is still available in Task Manager. This is how much RAM should be available in Task Manager while you are under load (on Windows Server 2003):
Physical RAM Target Avail RAM in Task Manager
< 4GB 512MB – 1GB
4-32GB 1GB – 2GB
32-128GB 2GB – 4GB
> 128GB > 4GB
You can use T-SQL to set your MaxServerMemory setting. The sample below sets it to 3500, which is the equivalent of 3.5GB. This setting is dynamic in SQL Server 2005/2008, which means that you can change it and it goes into effect immediately, without restarting SQL Server.
-- Turn on advanced optionsEXEC sp_configure'Show Advanced Options',1;GO
RECONFIGURE;GO
-- Set max server memory = 3500MB for the serverEXEC sp_configure'max server memory (MB)',3500;GO
RECONFIGURE;GO
-- See what the current values areEXEC sp_configure;You can also change this setting in the SSMS GUI, as you see below:

Finally, I have learned that it is a good idea to temporarily adjust your MaxServerMemory setting downward by a few GB if you know you will be doing a large file copy on your database server (such as copying a large database backup file).
http://www.sqlservercentral.com/blogs/glennberry/archive/2009/10/29/suggested-max-memory-settings-for-sql-server-2005_2F00_2008.aspx
Monday, September 20, 2010
Windows Server 2008/ 2008 R2 cannot ping setting
Configure Windows Firewall Settings – File and Printer Sharing
By default, Windows Firewall for WIndows Server 2008 is configured to disallow File and Printer Sharing on the network. By default Windows Server 2008 firewall is configured with Windows Firewall running, and with File and Printer Sharing disabled. This blocks ICMP Echo Request packets used by the PING command. You can allow the server to respond to ping requests by doing the following:
By default, Windows Firewall for WIndows Server 2008 is configured to disallow File and Printer Sharing on the network. By default Windows Server 2008 firewall is configured with Windows Firewall running, and with File and Printer Sharing disabled. This blocks ICMP Echo Request packets used by the PING command. You can allow the server to respond to ping requests by doing the following:
- Turn off Windows Firewall on the Windows 2008 Server (not recommended)- OR -
- Enable the File and Printer Sharing option in Windows Firewall Configuration Settings
- Start > Control Panel > Network and Intranet
- Under the Windows Firewall section heading, Click the Allow a program through Windows Firewall link
- In the programs and ports list, check the File and Printer Sharing option
Monitoring SQL Server disk I/O with PerfMon counters
As a DBA, you need to understand the I/O of your SQL Server disk subsystem. In part three of this screencast series, SQL Server MVP Kevin Kline explains how to track I/O in your direct-attached storage disks (DASD).
Get optimal throughput values to keep an eye on when using Performance Monitor counters for physical disk reads and writes and disk queue length. Kline also shares some best practices you can't afford to miss.
Video: http://searchsqlserver.techtarget.com/video/Monitoring-SQL-Server-disk-I-O-with-PerfMon-counters
Get optimal throughput values to keep an eye on when using Performance Monitor counters for physical disk reads and writes and disk queue length. Kline also shares some best practices you can't afford to miss.
Video: http://searchsqlserver.techtarget.com/video/Monitoring-SQL-Server-disk-I-O-with-PerfMon-counters
Friday, September 17, 2010
Chang to the Classic Logon Screen
Classic logon screen, where all user accounts are hidden from the Welcome screen and both a username and a password are required to log on, then do this:
Type secpol.msc in Vista's Start Menu Search Bar and hit Enter. This will open the Local Security Policy editor.
Navigate to Security Settings > Local Policies > Security Options
Look for Interactive Logon: Hide last username on the Right Hand Side. Set it to Enabled. Click Apply. Then close that window.
To Enable CTRL-ALT-DELETE Key Combo before login:
Type netplwiz in the Start Menu search box and hit Enter. This will open up the User Accounts dialog box. Select Advanced tab > Secure logon. Check Require users to press Ctrl+Alt+Delete. Click Apply. Then Reboot.
This guarantees that the authentic Windows logon prompt appears, protecting the system from programs that mimic a logon to retrieve passwords.
Type secpol.msc in Vista's Start Menu Search Bar and hit Enter. This will open the Local Security Policy editor.
Navigate to Security Settings > Local Policies > Security Options
Look for Interactive Logon: Hide last username on the Right Hand Side. Set it to Enabled. Click Apply. Then close that window.
To Enable CTRL-ALT-DELETE Key Combo before login:
Type netplwiz in the Start Menu search box and hit Enter. This will open up the User Accounts dialog box. Select Advanced tab > Secure logon. Check Require users to press Ctrl+Alt+Delete. Click Apply. Then Reboot.
This guarantees that the authentic Windows logon prompt appears, protecting the system from programs that mimic a logon to retrieve passwords.
Wednesday, September 15, 2010
How to Save Your Iphone / iphone 4 Battery Life
The iPhone 4 battery is supposedly 20% better than the 3GS and I still can’t go one full day without having to plug my iPhone in. I realized that I’m not the only one having this battery issue so I figured I’d post a few tips to maximize the iPhone battery life.
1. Make sure you kill those apps that are running in the background for nothing
2. Turn off wifi if you’re not using it (Settings > Wi-Fi and set Wi-Fi to Off)
3. Turn off 3G if you don’t need it (Settings > General > Network and set Enable 3G to Off)
4. Apple says Push can cause a 20% drop in battery life, but if you think yours is worse then it should be, the next step is to redo anything that involves Push, or Turn off Push Notifications (Settings > Notifications and set Notifications to Off)
5. Turn off Bluetooth (Settings > General > Bluetooth and set Bluetooth to Off)
6. Turn off Push Email (Settings > Mail, Contacts, Calendars > Fetch New Data and set Push to Off)
7. Fetch new data manually (Settings > Mail, Contacts, Calendars > Fetch New Data and tap Manually)
8. Go through a full charge cycle each month (charge the battery to 100% and completely run it down)
9. Turn off vibrate
10. Auto-adjust Brightness (Settings > Brightness and set Auto-Brightness to On)
1. Make sure you kill those apps that are running in the background for nothing
2. Turn off wifi if you’re not using it (Settings > Wi-Fi and set Wi-Fi to Off)
3. Turn off 3G if you don’t need it (Settings > General > Network and set Enable 3G to Off)
4. Apple says Push can cause a 20% drop in battery life, but if you think yours is worse then it should be, the next step is to redo anything that involves Push, or Turn off Push Notifications (Settings > Notifications and set Notifications to Off)
5. Turn off Bluetooth (Settings > General > Bluetooth and set Bluetooth to Off)
6. Turn off Push Email (Settings > Mail, Contacts, Calendars > Fetch New Data and set Push to Off)
7. Fetch new data manually (Settings > Mail, Contacts, Calendars > Fetch New Data and tap Manually)
8. Go through a full charge cycle each month (charge the battery to 100% and completely run it down)
9. Turn off vibrate
10. Auto-adjust Brightness (Settings > Brightness and set Auto-Brightness to On)
Tuesday, September 14, 2010
如何循序渐进向DotNet架构师发展
微软的DotNet开发绝对是属于那种入门容易提高难的技术。而要能够成为DotNet架构师没有三年或更长时间的编码积累基本上是不可能的。特别是在大型软件项目中,架构师是项目核心成员,承上启下,因此 RUP方法论也认同以架构为核心,体现4+1视图在整个软件开发过程中的重要作用。架构人员既要精通技术,又要熟悉业务,而且基本对软件生命周期各阶段的相关技术都需要有相关的积累和知识储备,而这些不经过多年的磨练是很难达到这个高度的。
要成为一个合格的架构师首先必须是一个合格或优秀的编码人员,对于开发来讲编码始终都是最重要的一项技能,在编码过程中只要自己善于去思考和分析问题,就 可以多学到很多相关的知识和技术。所以我们在开发过程中一定要注意新知识和新技术的学习,前人经验和成果的学习。编码过程中应该去思考的一些问题有:
1.在编码过程中自己是否做单元测试,是否使用相关工具做单元测试,如果没有的话是什么原因无法把单元测试做起来?
2.自己编码的泄露率情况,编码泄露的BUG的原因分析
3.是否有意识的对代码进行重构,重构过程中是否引入了相关设计模式的思想?
4.是否对C#语言的一些高级特性进行学习,如反射调用,异步处理等。
5.是否对Remoting和WebService两种分布式技术做过研究和对比分析?
6.是否经常研究开源项目和开源代码,如Duwamish,PetShop,NUnit,Enterprise Library,Nant等
7.是否对对象持久化机制和O/R Mapping等相关技术做过相关的研究
8.平时在编码过程中是否注重公用组件和公用类的复用和抽取
9.自己在平时工作和学习中是否经常开发些小工具提高工作效率,巩固学习知识
设计和编码其实是密切而不可分的,对于严格将设计和编码分开的瀑布模型一般也仅仅在大型项目中应用。而及时编码和设计分离,也不是将编码人员不需要思考, 编码活动始终是一项创造性的劳动,如果否定这个观点那就代表编码过程完全不需要人员介入而可以完全自动化。因此在这里谈设计主要还是指设计人员的系统化思 维能力,设计人员应该比开发人员站高一个层次来分析和思考问题。设计人员最重要的一个技能就是现实- >抽象的转换,而这个就需要谈到方法论的问题了,技术人员需要积累面对对象分析和设计或结构化分析知识的积累,需要有较强的数据库分析和设计能力。一个设计能否成为很好的架构师关键就在这种积累的深度和广度上面了。
因此在设计过程中应该考虑的问题有:
1.你现在分析和设计能力能否胜任大中型的应用系统还是只是独立功能分析和设计?
2.设计过程中是否有意识的考虑到组件的复用和相关接口设计准则。是否能够很自然的将分析模式,设计模式的相关内容应用到自己的设计过程中。
3.是否对XP,RUP,面向对象,结构化等方法论都有过较系统化的学习和思考。
4.是否真正理解系统功能需求和非功能需求对系统设计的不同的指导作用。
5.对自己设计的功能是否会根据后期的变更来反思自己的设计为何不能很好的适应变更?
6.是否在设计过程中经常自己开发些原型来对自己的设计思路进行验证?
7.是否专注技术的同时开始专业业务流程的分析,关注业务建模?
如果我们在设计和开发过程中经常关注这些知识和技能的话,成为一个合格的架构师是早晚的事情。平时能够胜任工作开发用到的知识和技能是微不足道的,如果自 己不是有意识的去学习这些知识的话,那技能是很难得到进一步提高的。我参加过两次微软的架构师培训,在北京的微软架构峰会上也有机会专门参加了 P&P Workshop的学习,培训老师是微软总部SmartClient Architecture and Design Guide一书的作者Edward A.Jezieski,让我感受最深是老外深刻的技术底蕴,对程序开发的执著。
对于DotNet架构经常用到的知识和技能储备有
1.RUP方法论,4+1视图。用例驱动业务建模- >分析模型- >设计模型
2.用例模式- >分析模式- >设计模式
3.常用的分布式技术
4.对安全,异常,日志,性能等非功能性需求的关注
5.对应用系统整体业务的关注
相关的一些参考书籍(微软网站和电驴都可以下载到)
微软网站提供的参考书籍
Enterprise Solution Patterns Using Microsoft.NET
.NET Data Access Architecture Guide
Application Architecture for .NET:Designing Applications and Services
Caching Architecture Guide for .NET Framework Applications
Designing Application-Managed Authorization
Smart Client Architecture and Design Guide
其它架构方面的参考书籍
Software Architecture In Practice
Pattern-Oriented Software Architecture
The Art Of Software Architecture
Beyond Software Architecture
模式方面的书籍
Analysis Patterns
Design Patterns-Elements of Reusable Object-Oriented Software
Applying UML and Patterns
Design Pattern***plained
要成为一个合格的架构师首先必须是一个合格或优秀的编码人员,对于开发来讲编码始终都是最重要的一项技能,在编码过程中只要自己善于去思考和分析问题,就 可以多学到很多相关的知识和技术。所以我们在开发过程中一定要注意新知识和新技术的学习,前人经验和成果的学习。编码过程中应该去思考的一些问题有:
1.在编码过程中自己是否做单元测试,是否使用相关工具做单元测试,如果没有的话是什么原因无法把单元测试做起来?
2.自己编码的泄露率情况,编码泄露的BUG的原因分析
3.是否有意识的对代码进行重构,重构过程中是否引入了相关设计模式的思想?
4.是否对C#语言的一些高级特性进行学习,如反射调用,异步处理等。
5.是否对Remoting和WebService两种分布式技术做过研究和对比分析?
6.是否经常研究开源项目和开源代码,如Duwamish,PetShop,NUnit,Enterprise Library,Nant等
7.是否对对象持久化机制和O/R Mapping等相关技术做过相关的研究
8.平时在编码过程中是否注重公用组件和公用类的复用和抽取
9.自己在平时工作和学习中是否经常开发些小工具提高工作效率,巩固学习知识
设计和编码其实是密切而不可分的,对于严格将设计和编码分开的瀑布模型一般也仅仅在大型项目中应用。而及时编码和设计分离,也不是将编码人员不需要思考, 编码活动始终是一项创造性的劳动,如果否定这个观点那就代表编码过程完全不需要人员介入而可以完全自动化。因此在这里谈设计主要还是指设计人员的系统化思 维能力,设计人员应该比开发人员站高一个层次来分析和思考问题。设计人员最重要的一个技能就是现实- >抽象的转换,而这个就需要谈到方法论的问题了,技术人员需要积累面对对象分析和设计或结构化分析知识的积累,需要有较强的数据库分析和设计能力。一个设计能否成为很好的架构师关键就在这种积累的深度和广度上面了。
因此在设计过程中应该考虑的问题有:
1.你现在分析和设计能力能否胜任大中型的应用系统还是只是独立功能分析和设计?
2.设计过程中是否有意识的考虑到组件的复用和相关接口设计准则。是否能够很自然的将分析模式,设计模式的相关内容应用到自己的设计过程中。
3.是否对XP,RUP,面向对象,结构化等方法论都有过较系统化的学习和思考。
4.是否真正理解系统功能需求和非功能需求对系统设计的不同的指导作用。
5.对自己设计的功能是否会根据后期的变更来反思自己的设计为何不能很好的适应变更?
6.是否在设计过程中经常自己开发些原型来对自己的设计思路进行验证?
7.是否专注技术的同时开始专业业务流程的分析,关注业务建模?
如果我们在设计和开发过程中经常关注这些知识和技能的话,成为一个合格的架构师是早晚的事情。平时能够胜任工作开发用到的知识和技能是微不足道的,如果自 己不是有意识的去学习这些知识的话,那技能是很难得到进一步提高的。我参加过两次微软的架构师培训,在北京的微软架构峰会上也有机会专门参加了 P&P Workshop的学习,培训老师是微软总部SmartClient Architecture and Design Guide一书的作者Edward A.Jezieski,让我感受最深是老外深刻的技术底蕴,对程序开发的执著。
对于DotNet架构经常用到的知识和技能储备有
1.RUP方法论,4+1视图。用例驱动业务建模- >分析模型- >设计模型
2.用例模式- >分析模式- >设计模式
3.常用的分布式技术
4.对安全,异常,日志,性能等非功能性需求的关注
5.对应用系统整体业务的关注
相关的一些参考书籍(微软网站和电驴都可以下载到)
微软网站提供的参考书籍
Enterprise Solution Patterns Using Microsoft.NET
.NET Data Access Architecture Guide
Application Architecture for .NET:Designing Applications and Services
Caching Architecture Guide for .NET Framework Applications
Designing Application-Managed Authorization
Smart Client Architecture and Design Guide
其它架构方面的参考书籍
Software Architecture In Practice
Pattern-Oriented Software Architecture
The Art Of Software Architecture
Beyond Software Architecture
模式方面的书籍
Analysis Patterns
Design Patterns-Elements of Reusable Object-Oriented Software
Applying UML and Patterns
Design Pattern***plained
Dedicated Hosting Offers 2010
GigeNET.com
http://www.webhostingtalk.com/showthread.php?t=975819&highlight=gigenet
http://www.webhostingtalk.com/showthread.php?t=963571&highlight=gigenet
http://www.webhostingtalk.com/showthread.php?t=956737&highlight=gigenet
http://www.webhostingtalk.com/showthread.php?t=975819&highlight=gigenet
http://www.webhostingtalk.com/showthread.php?t=963571&highlight=gigenet
http://www.webhostingtalk.com/showthread.php?t=956737&highlight=gigenet
The Cleverest Ways to Use Dropbox (Tips)
Free utility Dropbox is great at syncing files between computers, but it has a lot more potential than just that. Here's a handful of clever ways you can use Dropbox that you may not have thought of.
If you haven't read our first article on this subject, be sure to check out how to use Dropbox for more than just file syncing, where we covered using it to sync passwords across PCs, access portable applications from anywhere, or control your computer remotely. Let's add to those ideas and walk through a number of interesting use cases for Dropbox.

If data security is a big concern for you, create an encrypted TrueCrypt volume and store it in your Dropbox folder so you can sync it to anywhere. You can take it a step further by storing the portable version of TrueCrypt in your Dropbox folder as well, to save time if you need to get into your encrypted volume from a PC that isn't already hooked into Dropbox. Aren't too familiar with TrueCrypt? Check out our beginner's guide to get you started.
Once you've got your TrueCrypt volume up and running, you can install all of your portable applications, documents, and anything else you want to keep completely secure. You might be concerned about syncing such a large file between PCs, but since Dropbox only transfers the part of the file that has actually changed, there shouldn't be too much bandwidth being used.
 Over at How-To Geek, since our team is geographically all over the map, we use Dropbox's shared folders feature to simulate the type of shared network drive you might find in a corporate environment. We store all of our important files like business documents, artwork, and other files, in our shared folder—whenever any of us changes a file, the rest of us get the changed version in seconds.
Over at How-To Geek, since our team is geographically all over the map, we use Dropbox's shared folders feature to simulate the type of shared network drive you might find in a corporate environment. We store all of our important files like business documents, artwork, and other files, in our shared folder—whenever any of us changes a file, the rest of us get the changed version in seconds.
The really great feature that sets Dropbox apart from the rest as a shared network drive for a team is the file revisions—whether a file gets accidentally deleted, or much more commonly, overwritten with a bad version, you can easily recover the older version of the file through the web interface.
 One of the complaints many people have about Dropbox is that it's actually a separate folder, and you have to remember to put your documents there in order to have them be synced, rather than just specifying particular folders to sync. Instead of remembering, you can actually change your My Documents folder to be the same as your Dropbox folder, or be in a folder inside your Dropbox.
One of the complaints many people have about Dropbox is that it's actually a separate folder, and you have to remember to put your documents there in order to have them be synced, rather than just specifying particular folders to sync. Instead of remembering, you can actually change your My Documents folder to be the same as your Dropbox folder, or be in a folder inside your Dropbox.
To do so for Windows 7 or Vista, just right-click on your Documents folder, select Properties, and then on the Location tab you can specify the new file path, and click the Move button. The process is very similar in Windows XP, but you'll need to change the Target value instead.
If you don't want to move your documents folder, but still want quick access, be sure to check out how to add your Dropbox folder to the Windows 7 Start Menu.
 Since Dropbox makes it easy to create publicly shared files accessible through a URL, you can create your own customized start page for your browser, complete with bookmarks and anything else your HTML skills and imagination can come up with. This can be especially useful for your mobile device, where start pages aren't always tailored to what you might really want. Just create the HTML file, store it in your Public folder, and then grab the public URL from the Dropbox context menu to set as your start page.
Since Dropbox makes it easy to create publicly shared files accessible through a URL, you can create your own customized start page for your browser, complete with bookmarks and anything else your HTML skills and imagination can come up with. This can be especially useful for your mobile device, where start pages aren't always tailored to what you might really want. Just create the HTML file, store it in your Public folder, and then grab the public URL from the Dropbox context menu to set as your start page.
If your HTML skills are lacking, you can check out this tutorial from reader elasticthreads, who has a custom search page using the web-command-line service YubNub to make quick work of searching from your mobile device using a number of services, like Google Images, Maps, or Amazon.

Rather than wait until you get back home to start a download, why not start them remotely from anywhere? All you have to do is set your torrent client to monitor a folder in your Dropbox, and then add the torrent files to the folder remotely—you can even upload them through the web interface if you want. Most of the popular torrent clients, like uTorrent, support this feature, and while there are other ways to remotely start a download, this is certainly one of the easiest.
Reader @joeattardi has an even more clever use: he downloads PDF files from restaurants with nutrition facts, so he can get informed nutrition data while he's on the go. The same technique could be used for all sorts of helpful information—quick shortcut guides, useful fact sheets, or anything else you can imagine and might need while you're away from your PC.
 If you're an iTunes user, moving your library to your Dropbox folder is easy—first, make sure iTunes is closed, then move your iTunes music folder into your Dropbox folder. Then just hold down the Shift key (or Option for Macs) while you open iTunes, and you'll be presented with a prompt to choose which iTunes library to use, so choose the folder from the new location.
If you're an iTunes user, moving your library to your Dropbox folder is easy—first, make sure iTunes is closed, then move your iTunes music folder into your Dropbox folder. Then just hold down the Shift key (or Option for Macs) while you open iTunes, and you'll be presented with a prompt to choose which iTunes library to use, so choose the folder from the new location.
On the secondary PC, you can just use the Shift key trick to choose the folder from the new location in your Dropbox.
 Once all your music is over on your Dropbox, you can access it through the web interface from any web browser, including your iPhone or some other web-connected devices. It might not be the perfect web-based music interface, but it's certainly functional enough to use.
Once all your music is over on your Dropbox, you can access it through the web interface from any web browser, including your iPhone or some other web-connected devices. It might not be the perfect web-based music interface, but it's certainly functional enough to use.
Source: http://lifehacker.com/5527055/the-cleverest-ways-to-use-dropbox-that-youre-not-using
If you haven't read our first article on this subject, be sure to check out how to use Dropbox for more than just file syncing, where we covered using it to sync passwords across PCs, access portable applications from anywhere, or control your computer remotely. Let's add to those ideas and walk through a number of interesting use cases for Dropbox.
Store Your Files in an Encrypted TrueCrypt Volume

If data security is a big concern for you, create an encrypted TrueCrypt volume and store it in your Dropbox folder so you can sync it to anywhere. You can take it a step further by storing the portable version of TrueCrypt in your Dropbox folder as well, to save time if you need to get into your encrypted volume from a PC that isn't already hooked into Dropbox. Aren't too familiar with TrueCrypt? Check out our beginner's guide to get you started.
Once you've got your TrueCrypt volume up and running, you can install all of your portable applications, documents, and anything else you want to keep completely secure. You might be concerned about syncing such a large file between PCs, but since Dropbox only transfers the part of the file that has actually changed, there shouldn't be too much bandwidth being used.
Use Shared Folders as a Cheap Network Drive for Remote Teams
 Over at How-To Geek, since our team is geographically all over the map, we use Dropbox's shared folders feature to simulate the type of shared network drive you might find in a corporate environment. We store all of our important files like business documents, artwork, and other files, in our shared folder—whenever any of us changes a file, the rest of us get the changed version in seconds.
Over at How-To Geek, since our team is geographically all over the map, we use Dropbox's shared folders feature to simulate the type of shared network drive you might find in a corporate environment. We store all of our important files like business documents, artwork, and other files, in our shared folder—whenever any of us changes a file, the rest of us get the changed version in seconds.The really great feature that sets Dropbox apart from the rest as a shared network drive for a team is the file revisions—whether a file gets accidentally deleted, or much more commonly, overwritten with a bad version, you can easily recover the older version of the file through the web interface.
Make Dropbox Your Actual "My Documents" Folder
 One of the complaints many people have about Dropbox is that it's actually a separate folder, and you have to remember to put your documents there in order to have them be synced, rather than just specifying particular folders to sync. Instead of remembering, you can actually change your My Documents folder to be the same as your Dropbox folder, or be in a folder inside your Dropbox.
One of the complaints many people have about Dropbox is that it's actually a separate folder, and you have to remember to put your documents there in order to have them be synced, rather than just specifying particular folders to sync. Instead of remembering, you can actually change your My Documents folder to be the same as your Dropbox folder, or be in a folder inside your Dropbox.To do so for Windows 7 or Vista, just right-click on your Documents folder, select Properties, and then on the Location tab you can specify the new file path, and click the Move button. The process is very similar in Windows XP, but you'll need to change the Target value instead.
If you don't want to move your documents folder, but still want quick access, be sure to check out how to add your Dropbox folder to the Windows 7 Start Menu.
Create Your Own Customized Browser Start Page
 Since Dropbox makes it easy to create publicly shared files accessible through a URL, you can create your own customized start page for your browser, complete with bookmarks and anything else your HTML skills and imagination can come up with. This can be especially useful for your mobile device, where start pages aren't always tailored to what you might really want. Just create the HTML file, store it in your Public folder, and then grab the public URL from the Dropbox context menu to set as your start page.
Since Dropbox makes it easy to create publicly shared files accessible through a URL, you can create your own customized start page for your browser, complete with bookmarks and anything else your HTML skills and imagination can come up with. This can be especially useful for your mobile device, where start pages aren't always tailored to what you might really want. Just create the HTML file, store it in your Public folder, and then grab the public URL from the Dropbox context menu to set as your start page.If your HTML skills are lacking, you can check out this tutorial from reader elasticthreads, who has a custom search page using the web-command-line service YubNub to make quick work of searching from your mobile device using a number of services, like Google Images, Maps, or Amazon.
Start Your Torrents from Any Computer

Rather than wait until you get back home to start a download, why not start them remotely from anywhere? All you have to do is set your torrent client to monitor a folder in your Dropbox, and then add the torrent files to the folder remotely—you can even upload them through the web interface if you want. Most of the popular torrent clients, like uTorrent, support this feature, and while there are other ways to remotely start a download, this is certainly one of the easiest.
Take Useful Information With You
Since you can easily sync your data to your iPhone, or access files through the mobile web interface, you can keep your collection of PDF books or other files in your Dropbox folder. You can use this to turn your iPhone, iPad, or other mobile device into an eBook reader from anywhere.Reader @joeattardi has an even more clever use: he downloads PDF files from restaurants with nutrition facts, so he can get informed nutrition data while he's on the go. The same technique could be used for all sorts of helpful information—quick shortcut guides, useful fact sheets, or anything else you can imagine and might need while you're away from your PC.
Sync Your Music, Access from Anywhere, or Share With Friends
Having access to your music collection from anywhere is always a favorite technique for any web-based sync system, and Dropbox is no slouch in that department. You can put your entire music collection in your Dropbox folder and keep it in sync between all of your PCs, as well as listen through the web interface. If you're an iTunes user, moving your library to your Dropbox folder is easy—first, make sure iTunes is closed, then move your iTunes music folder into your Dropbox folder. Then just hold down the Shift key (or Option for Macs) while you open iTunes, and you'll be presented with a prompt to choose which iTunes library to use, so choose the folder from the new location.
If you're an iTunes user, moving your library to your Dropbox folder is easy—first, make sure iTunes is closed, then move your iTunes music folder into your Dropbox folder. Then just hold down the Shift key (or Option for Macs) while you open iTunes, and you'll be presented with a prompt to choose which iTunes library to use, so choose the folder from the new location.On the secondary PC, you can just use the Shift key trick to choose the folder from the new location in your Dropbox.
 Once all your music is over on your Dropbox, you can access it through the web interface from any web browser, including your iPhone or some other web-connected devices. It might not be the perfect web-based music interface, but it's certainly functional enough to use.
Once all your music is over on your Dropbox, you can access it through the web interface from any web browser, including your iPhone or some other web-connected devices. It might not be the perfect web-based music interface, but it's certainly functional enough to use.Source: http://lifehacker.com/5527055/the-cleverest-ways-to-use-dropbox-that-youre-not-using
Monday, September 13, 2010
盲婚記 三 生命在於運動 (2)
生命在于运动,用这句话来总结二孬的前小半辈子,再贴切不过。不止是他爱运动,运动也很爱他。
二孬的青葱岁月,刻录下来的都是他那个年代人都有的轨迹。跟着奶奶要饭被狗咬伤的童年,饿的发昏读书的少年,进了大学等着分工作的青年。作为得意门生,二孬子被班主任告知,毕业即留校,留在离家只几个钟头车的西安。大局一定,他欢天喜地的跟着同学看电影去了。
那部电影,叫五朵金花。
金花的美丽,云南的神秘,轻松洗掉了二孬的理智。当支援大西南的运动开始的时候,二孬递上了自己的申请。他的原意,只想做个姿态,保持他一贯上进的风格。然而事实证明,侥幸就像彩票,赌的人多,中的人少。
老师的扼腕,二孬的愕然,都没有挡住开往云南的火车。二孬第一次为自己做抉择,惨败。
在火车上,来接他们的老郭给这群头脑简单,目的单纯的热血青年们描画了一副蓝图。那里,有金花一样美丽的女孩子,那里有热情的红土高原,那里有可以抛头颅撒热血的天空,那里,有不会辜负你期望的惊喜。
二孬把这些话记在心里,狠狠的想像着西南边陲的奇异景象。大象是当街走的,孔雀是天上飞的,香蕉是长在路边随手摘的,阿妹是唱歌不讲话的。
很多年以后,当购物频道刚刚兴起的时候,二孬很不屑的评论说,这招,早有人用过了。二孬的女儿更不屑的说,对,还总是有人要上当。你们当年,说的好听就是支援大西南开发,实质就是卖猪崽到南洋打工,进步的只是多了2位代言人,不,是6位,5个金花,一个阿诗玛。
真相往往需要很大的勇气来面对。二孬真的站在金花的土地上,感到了很真切的茫然和失落。没有漫天飞舞的蝴蝶,也没有来来往往的大象。唯一比较符合的片断是女孩子。她们和金花一样。。。。黝黑矮小。可是那时,小麦色还不流行;那时,野蛮女友还没发明。
和二孬一起的还有他的很多同学,都是受了感召,穿了大半个中国,来到这历史中的蛮荒之地。虽然偏僻,昆明这个小小地方却还不至于让他们的满腔热血瞬时消失殆尽。这里的天空很蓝,这里的气候很好,这里的东西很奇特,这里的人很热情。很快,二孬兴致勃勃的写信报告他爹娘,儿一切安好,吃得饱穿得暖,这里风光明媚,四季宜人。只是挂念娘做得布袜,多多做些来才好。
于是工作了许久,二孬定期还是收到家里寄来手工缝制得布袜棉衫,穿上身,仿佛娘得手,粗粗得温暖得护着他。
二孬的青葱岁月,刻录下来的都是他那个年代人都有的轨迹。跟着奶奶要饭被狗咬伤的童年,饿的发昏读书的少年,进了大学等着分工作的青年。作为得意门生,二孬子被班主任告知,毕业即留校,留在离家只几个钟头车的西安。大局一定,他欢天喜地的跟着同学看电影去了。
那部电影,叫五朵金花。
金花的美丽,云南的神秘,轻松洗掉了二孬的理智。当支援大西南的运动开始的时候,二孬递上了自己的申请。他的原意,只想做个姿态,保持他一贯上进的风格。然而事实证明,侥幸就像彩票,赌的人多,中的人少。
老师的扼腕,二孬的愕然,都没有挡住开往云南的火车。二孬第一次为自己做抉择,惨败。
在火车上,来接他们的老郭给这群头脑简单,目的单纯的热血青年们描画了一副蓝图。那里,有金花一样美丽的女孩子,那里有热情的红土高原,那里有可以抛头颅撒热血的天空,那里,有不会辜负你期望的惊喜。
二孬把这些话记在心里,狠狠的想像着西南边陲的奇异景象。大象是当街走的,孔雀是天上飞的,香蕉是长在路边随手摘的,阿妹是唱歌不讲话的。
很多年以后,当购物频道刚刚兴起的时候,二孬很不屑的评论说,这招,早有人用过了。二孬的女儿更不屑的说,对,还总是有人要上当。你们当年,说的好听就是支援大西南开发,实质就是卖猪崽到南洋打工,进步的只是多了2位代言人,不,是6位,5个金花,一个阿诗玛。
真相往往需要很大的勇气来面对。二孬真的站在金花的土地上,感到了很真切的茫然和失落。没有漫天飞舞的蝴蝶,也没有来来往往的大象。唯一比较符合的片断是女孩子。她们和金花一样。。。。黝黑矮小。可是那时,小麦色还不流行;那时,野蛮女友还没发明。
和二孬一起的还有他的很多同学,都是受了感召,穿了大半个中国,来到这历史中的蛮荒之地。虽然偏僻,昆明这个小小地方却还不至于让他们的满腔热血瞬时消失殆尽。这里的天空很蓝,这里的气候很好,这里的东西很奇特,这里的人很热情。很快,二孬兴致勃勃的写信报告他爹娘,儿一切安好,吃得饱穿得暖,这里风光明媚,四季宜人。只是挂念娘做得布袜,多多做些来才好。
于是工作了许久,二孬定期还是收到家里寄来手工缝制得布袜棉衫,穿上身,仿佛娘得手,粗粗得温暖得护着他。
盲婚記 三 生命在於運動 (1)
基本上两个人都直接漠视了他们女儿的外婆,墨馨她娘的存在,除了吵架的时候。那时侯固定的台词是:要不是你(我)妈,我怎么会娶 (嫁)了你。从懂事起,二孬的女儿——差点被取名“四大”的二妞,就无师自通了一个人生真理
“不做媒人三代好”。
虽然,她的婚姻还是靠了媒人间接解决了,可只要不是自己当媒人,祸害的不是自己的后代,那总是没关系的。二妞到了自己要生小孩儿的时候才想到,要是这个说法有效,从外婆开始算,她正好是媒人的第三代。
对此,她娘墨馨说,胡说。媒字儿怎么写,女 某,有甘露有树木,这样的女人子孙才旺呢。可当年墨馨和二孬吵架的时候还说过,我娘走霉运了才遇到你。
没错,遇到二孬的时候,墨馨她娘正是霉人,倒霉的人。
墨馨她娘,3个女儿,一个儿子的娘,那会儿正如火如荼的下放在农村,进行着由黑到白的改造。二孬也是,正在他单位所属的农场,由食堂炊事员李秀莲同志看管,进行深刻到要触及灵魂的反省。墨馨她娘就不说了,复杂的家庭出身,争强好胜的行事作风,动乱来了,不借机拿出来整治一下,简直就是暴殄天物,资源浪费。于是负着各种同情奚落幸灾乐祸的目光,她娘带着最小的儿子,提着两个小包,一杆子扎到了最穷的农村。血统优良根红苗正的二孬怎么也划归了黑五类呢?让我们从头讲起。
“不做媒人三代好”。
虽然,她的婚姻还是靠了媒人间接解决了,可只要不是自己当媒人,祸害的不是自己的后代,那总是没关系的。二妞到了自己要生小孩儿的时候才想到,要是这个说法有效,从外婆开始算,她正好是媒人的第三代。
对此,她娘墨馨说,胡说。媒字儿怎么写,女 某,有甘露有树木,这样的女人子孙才旺呢。可当年墨馨和二孬吵架的时候还说过,我娘走霉运了才遇到你。
没错,遇到二孬的时候,墨馨她娘正是霉人,倒霉的人。
墨馨她娘,3个女儿,一个儿子的娘,那会儿正如火如荼的下放在农村,进行着由黑到白的改造。二孬也是,正在他单位所属的农场,由食堂炊事员李秀莲同志看管,进行深刻到要触及灵魂的反省。墨馨她娘就不说了,复杂的家庭出身,争强好胜的行事作风,动乱来了,不借机拿出来整治一下,简直就是暴殄天物,资源浪费。于是负着各种同情奚落幸灾乐祸的目光,她娘带着最小的儿子,提着两个小包,一杆子扎到了最穷的农村。血统优良根红苗正的二孬怎么也划归了黑五类呢?让我们从头讲起。
盲婚記 二 墨馨的童年
二孬子的媳妇儿,从出生开始就和他全然不同。如火如荼的解放战争,漫天的轰炸和四处躲避的人群,他的媳妇儿就在这么不堪的热闹中诞生了。生下来的时候,哭声凄厉而清冽,仿佛知道因为改朝换代,她那个显赫了几世得家族终于衰落了。
二孬子家的血统,是纯的不能再纯的贫农。传到他这辈,终于有了起色。让我们来看看,基因怎么突变了。首先是二孬子的几个哥哥。本家的几个哥哥,因为老吃不饱怒了,于是趁夜黑风高的时候跟了共产党投奔自由。这一解放,都做了官儿,世代农民的血液就散出了达官显贵的味道。二孬子托了村子里启蒙老师的福,学习大好,于是在高二那年提前考进大学,成了秀才。这下齐了,二孬子家混入了当时时兴的各种元素,由最受压迫的贫农摇身一变成了社会新贵。
和二孬子家得扬眉吐气相反,他媳妇儿家昔日的种种权势,因着大环境的改变,一夜变成重重的枷锁,把整个家族压到了社会最底层。虽然败落了,二孬媳妇还是享受了及其奢华得童年。四进得大院子,胖胖得奶妈,保姆叫腊梅,粗使丫鬟夏菊,早餐桌上烤得焦焦得面包和黄油,院子里长了一百多年得梅花和枝繁叶茂得桂花,香香得味道浸润了她整个童年。二孬媳妇每次想起来都无限回味得说,这才叫生活。忘了介绍,二孬媳妇是长房长女,闺名墨馨。
如果是拍电视剧,应该是这样得。这边厢墨馨让保姆伺候着优雅得吃着面包黄油,那边厢二孬茫然得跟着小脚奶奶沿街要饭。
就是这么两个截然不同得人,最后走到了一起。二孬子总是深情得说,感谢党,感谢新中国。墨馨总是惆怅得说,要不是党,要不是新中国。
二孬子家的血统,是纯的不能再纯的贫农。传到他这辈,终于有了起色。让我们来看看,基因怎么突变了。首先是二孬子的几个哥哥。本家的几个哥哥,因为老吃不饱怒了,于是趁夜黑风高的时候跟了共产党投奔自由。这一解放,都做了官儿,世代农民的血液就散出了达官显贵的味道。二孬子托了村子里启蒙老师的福,学习大好,于是在高二那年提前考进大学,成了秀才。这下齐了,二孬子家混入了当时时兴的各种元素,由最受压迫的贫农摇身一变成了社会新贵。
和二孬子家得扬眉吐气相反,他媳妇儿家昔日的种种权势,因着大环境的改变,一夜变成重重的枷锁,把整个家族压到了社会最底层。虽然败落了,二孬媳妇还是享受了及其奢华得童年。四进得大院子,胖胖得奶妈,保姆叫腊梅,粗使丫鬟夏菊,早餐桌上烤得焦焦得面包和黄油,院子里长了一百多年得梅花和枝繁叶茂得桂花,香香得味道浸润了她整个童年。二孬媳妇每次想起来都无限回味得说,这才叫生活。忘了介绍,二孬媳妇是长房长女,闺名墨馨。
如果是拍电视剧,应该是这样得。这边厢墨馨让保姆伺候着优雅得吃着面包黄油,那边厢二孬茫然得跟着小脚奶奶沿街要饭。
就是这么两个截然不同得人,最后走到了一起。二孬子总是深情得说,感谢党,感谢新中国。墨馨总是惆怅得说,要不是党,要不是新中国。
盲婚記 第一章 六小龄童
1940年,河南某偏僻的农村,二孬子寂静无声的来到了这个世界。因为生下来许久都不会哭,他爹对他娘说,咦,看你生的这个儿子,哭都不会,真孬。加上在家排行第二,这个不算白胖的孩子被冠名二孬。
二孬就这样被叫了许多年,久到几十年后,当他带着初长成的女儿出现在村口的时候,凭着一句“俺是二孬”瞬间集合了一批热情的村民,颇有敲锣打鼓的功效。离开的这些年,都被“二孬”这个看似普遍而韵味独特的标签灰一样的吹散,那一刻,二孬觉得他穿越了,回到了村边的池塘,光着屁股捏着乱跳的小鱼,欢快的准备献给他娘。正要觉得后腚凉嗖嗖的时候,手里的鱼儿跳脱了掌握,低头一看,哦,女儿的手给他捏得快断了。
这是他得女儿第一次理解到,原来父亲给当初自己取名“四大”是很有历史渊源得。二孬和四大,都是以量词开头,形容词结尾。相较而言,“大”比“孬”更上升了几个档次,不仅读音响亮,意义也无比优美。于是,女儿很是同情了一下父亲,长得象猪头不是错,叫猪头也不是错,可是长得象猪头而每个人都坚持叫你猪头,那就是一个非常悲哀得错。
二孬子虽然出生得时候不会哭,可是后来声音洪亮无比,可传千里,很快被挑上选去学了豫剧。逢着赶集得日子,总能看见他在台上鲜活得唱念做打,男女兼顾演出着别人得悲欢离合生生死死。时年6岁,江湖传曰:六小龄童。
二孬子得爹娘对此持截然不同得意见。他娘觉得,这孩儿学这些没用,瞎耽误功夫;他爹反而觉着,看我这孩儿,真本事,6岁都会唱戏,又有人管饭,还能让他爹去后台看戏,将来实在没饭吃,靠这个也能混个瓜儿枣儿的。他爹娘意见再怎么不统一,这也还是人民内部矛盾,对外一致宣称的是:俺们不管,这是孩子的造化。不赞成也不反对,深得外交部发言人得要领。
二孬子戏唱得好,他的老师也顺理成章的因此喜欢他,整天逼着他练签名外加课外辅导,怕他将来出息了字儿卻写不好,问起来原来是师之惰,那就不好在村里混了。于是二孬成天写字算算术,家里的土墙实在画不下了,他爹便捉了许多乌龟来让他练手。发展到后来,池塘的乌龟终于销声匿迹了,二孬也小学毕业了。至今,二孬的毛笔字和画风流畅大气,尤其草体,看起来都跟甲骨文似的。
当二孬子以9岁高龄还光着屁股四周围游走的时候,他后来的媳妇儿,在祖国西南边陲之地,在四处轰炸的隆隆炮声中,哭喊着为他到来了。
二孬就这样被叫了许多年,久到几十年后,当他带着初长成的女儿出现在村口的时候,凭着一句“俺是二孬”瞬间集合了一批热情的村民,颇有敲锣打鼓的功效。离开的这些年,都被“二孬”这个看似普遍而韵味独特的标签灰一样的吹散,那一刻,二孬觉得他穿越了,回到了村边的池塘,光着屁股捏着乱跳的小鱼,欢快的准备献给他娘。正要觉得后腚凉嗖嗖的时候,手里的鱼儿跳脱了掌握,低头一看,哦,女儿的手给他捏得快断了。
这是他得女儿第一次理解到,原来父亲给当初自己取名“四大”是很有历史渊源得。二孬和四大,都是以量词开头,形容词结尾。相较而言,“大”比“孬”更上升了几个档次,不仅读音响亮,意义也无比优美。于是,女儿很是同情了一下父亲,长得象猪头不是错,叫猪头也不是错,可是长得象猪头而每个人都坚持叫你猪头,那就是一个非常悲哀得错。
二孬子虽然出生得时候不会哭,可是后来声音洪亮无比,可传千里,很快被挑上选去学了豫剧。逢着赶集得日子,总能看见他在台上鲜活得唱念做打,男女兼顾演出着别人得悲欢离合生生死死。时年6岁,江湖传曰:六小龄童。
二孬子得爹娘对此持截然不同得意见。他娘觉得,这孩儿学这些没用,瞎耽误功夫;他爹反而觉着,看我这孩儿,真本事,6岁都会唱戏,又有人管饭,还能让他爹去后台看戏,将来实在没饭吃,靠这个也能混个瓜儿枣儿的。他爹娘意见再怎么不统一,这也还是人民内部矛盾,对外一致宣称的是:俺们不管,这是孩子的造化。不赞成也不反对,深得外交部发言人得要领。
二孬子戏唱得好,他的老师也顺理成章的因此喜欢他,整天逼着他练签名外加课外辅导,怕他将来出息了字儿卻写不好,问起来原来是师之惰,那就不好在村里混了。于是二孬成天写字算算术,家里的土墙实在画不下了,他爹便捉了许多乌龟来让他练手。发展到后来,池塘的乌龟终于销声匿迹了,二孬也小学毕业了。至今,二孬的毛笔字和画风流畅大气,尤其草体,看起来都跟甲骨文似的。
当二孬子以9岁高龄还光着屁股四周围游走的时候,他后来的媳妇儿,在祖国西南边陲之地,在四处轰炸的隆隆炮声中,哭喊着为他到来了。
盲婚記 序
我们家两代人, 都是盲婚, 在这个年代的中国, 怕是没有几个能有资格称得上这个词. 所以我想, 用盲婚记来做名字, 很好很强大.
我父母的故事, 跟现今的热门话题都没有关系. 没有小三, 没有婚外恋, 连最低等级的曖昧暗恋都不沾边. 往大了说, 最多也就异地分居能靠得上. 可是我是这样的爱这个故事, 爱着他们, 留连在这裡寻找生活的勇气和信心.
我父母的故事, 跟现今的热门话题都没有关系. 没有小三, 没有婚外恋, 连最低等级的曖昧暗恋都不沾边. 往大了说, 最多也就异地分居能靠得上. 可是我是这样的爱这个故事, 爱着他们, 留连在这裡寻找生活的勇气和信心.
Sunday, September 12, 2010
移居美国后,再回头看中国——我的真实经历!(转载)
source: http://www.huaren.us/dispbbs.asp?boardid=331&id=803904&page=0&star=1
这篇文章的内容已经在心中积蓄很久了,不是一两天,也不是一两个月.一直难以下笔,实在是因为自己也是被骂者的同 类,损敌一千,自伤八百.无奈最后水满自溢, 还是忍不住从脑子里破堤而出,落在了笔端.把草稿拿给几个朋友看,有的说好,中肯;也有的说我太刻薄,伤人.也有的说:你找死啊?写这样的东西!就让我心 里特犹豫,要不要发出来啊?最后就借着点酒,贴了.酒壮SONG_二声(这个字的中文到底怎么写啊?字典里查不出来)人胆,一点不假.只是脑子里一直闪现 着儿时看过的一场电影,里面的主角对着步话机大声喊:向我开炮! 这几句话算是前言吧!
到中国旅游,本是一件非常愉快的事情,尤其带着儿子,让他们从小能够切身体会一下中国的风土人情,到各个历史景点感受一下中国的文化传承,真是胜过书本上一万个对长城,故宫,兵马佣介绍的文字与图片
只是,有所得也必有所失.在让儿子去感受中国悠久历史文化的熏陶的同时,也无可避免地会让他们目睹着当今中国社会各式各样的丑行,弄得儿子常常向我 提一些令我尴尬不知如何回答的问题.譬如,为什么街上的气车从来不让行人?为什么到处都那么脏,大家随便往地上扔东西? 为什么人们那么粗鲁没有礼貌?为什么又脏又臭的厕所门口总会有人收钱?为什么人们讲话那么大声好象在吵架?为什么那么多的人不分场合在哪里都抽烟?为什么 每到一个地方总有那么多的人扑过来非要卖东西给你而且缠着不走?其实答案不是没有,只是我不想说,因为我不愿意让他们在心中种下太多对中国负面的印象,尽 管我知道我的努力最终可能仍会是徒劳
孩子很小的时候,我们就开始带他们往中国跑了,目的是趁他们年纪还小,还能够对我们 的安排没有提出异议时,让他们尽早地习惯中国的状况.因为我们看到周围很多的朋友,等到孩子十几岁了,认为懂事了,有理解能力,能够吸收一路的所见所闻 了,于是带着去中国,满怀期望地想让孩子去感受中国的历史与文化,去了解自己作为中国人的根,而结果却往往是趁兴而去,扫兴而归.最典型的效果就是,回来 后孩子们做总结一般地对父母说:那就是你们出生长大的地方啊!语气中带着明显的失望与不屑,并拒绝以后再去.这个时候,弄得做父母的一只手伸了起来,不知 道是应该抽孩子的嘴巴,还是往自己脸上煽
中国这几十年经济发展突飞猛进,全世界都有目共睹.譬如说上海,几个月不去,就会展 现出一片崭新的市容.记得95年去上海,当空中小姐宣布我们已经飞临上海的天空时,我从飞机上向下望去,看到的只是一片漆黑.当我的兄弟接上我, 穿过无灯的黑暗,驱车行驶在上海市区那坑坑凹凹高低不平,恨不得能把肠子都颠腾出来的的街道上时,夜色之中,我看到的上海完全是一个庞大无比的建筑工地, 道路两旁以至绵延到天边的全是高耸入云的脚手架印在空中的影子;几年后再去上海,夜幕之下,我发现它已经完全成了灯火通明,高楼成群的花花世界了,比纽约 还要气势!当我一次从上海绕道香港回到美国,向太太描绘这这个崭新的世界时,太太凭着她八十年代的记忆,完全没有能力接受,这个在她嘴里一直是个”破上 海”的地方都快比她的香港还要繁华了.当然,如果我要是告诉她,上海外滩旁边的停车场里帮司机寻找车位的老头,身上的西服与领带比微软总裁比尔.盖兹穿得 还要正式气派,那还不如告诉她,我从上海到香港其实是脚踏着阿拉伯人的地毯而不是买票坐的飞机 ,所以我没有提起
遗憾的是,中国的经济发展,人们物质生活水平的提高,并没有相应地带来社会道德的提升.和谐社会的口号之所以如此响亮地提出,也同样响亮地说明,这个社会多么缺少和谐
这几年往中国跑了不知道多少次了,以我个人的经历所总结出来的这个社会的状况让我实在不敢恭维.这个社会缺少人与人之间的基本的尊敬,缺少人与人之 间的起码的信任,更缺少人与人之间最根本的平等相处的观念.古人曾说:仓廪实而知礼节.看着如今的中国社会, 我只能说,我们的古人太天真善良了
在中国,我每每看到公司里的主管面对下属,如何以在美国完全可以被视为人身攻击的方式进行训斥和辱骂,而同一个下属当他/她点头哈腰地承受了上司如 此的辱骂之后,转过身去便将同样的待遇抛给他/她的下属;而在街头上,则更不用说了.我在北京中关村,曾目击过一个警察如何象流氓一样欺辱讹诈一个骑板车 的民工,而这个民工却自始至终满脸谗笑不敢回一句话;也在浙江义乌的火车站,看到另一个骑板车的民工如何凶蛮地当着众人的面,狠狠地抽一个应该是比他地位 更底的刚进城的乡下人耳光
我有时与朋友开玩笑道:中国是一个从上往下煽耳光,从下往上磕头的社会,这个社会里人们没有平等,据说已经消灭了阶级,但却充满了无数等级森严贵贱分明的阶层
为了不用磕头而可以坚定地站到煽耳光的行列之中,这个社会充斥着种种的荒诞:
这个社会造就了每个人出门时,无论时间场合,都要穿上最漂亮最贵重的衣服,以在公众场合显示自己很有身份,从而获取别人的尊重;
这个社会造就了即便上班骑车也不过十分钟,开车却要堵半个小时,而仍然前仆后继争相购买私家车的人群,以显示自己富有与高人一等;
这个社会造就了全民族的小心谨慎,永远带着怀疑的眼光审视着周围的人群,害怕被骗,也常常被骗,有了机会也毫不迟疑地去骗别的傻瓜以显示自己的机警与聪明;
这个社会造就了全民族的狗眼病,在与别人的初次接触时, 每个人都隔着大脑中的门缝细心揣摩对方的身价与身份,在自己心中暗暗排列高低的档位,然后逐一划归属于要向他/她磕头的一族,或是将来有机会可以煽耳光的一类;
这个社会造就出与人交往时,如果你客气礼貌地对人说话,人家定会以为你身份卑微,或者有求于人,于是对你横眉竖眼,不屑正视;而你故意扯起了嗓子,一副土匪的样子高声吆喝,别人却会立即对你点头哈腰,唯唯喏喏,生怕一不小心得罪了不知道有着什么背景的何方神圣
这个社会造就了另一个严重的被称之为红眼病的流行病,每个人都觉得别人比自己挣到了更多的钱,于是每个人都削尖了脑袋挖尽心思要比别人捞更多的钱, 生活的重心仿佛除了钱还是钱.商人为了钱,可以黑着心卖没有营养的婴儿奶粉,让无数喝了它的婴儿终生残疾;农民为了钱,可以用各种化学原料施于水果之中让 它们显得鲜嫩可口,让吃过的人中毒至癌;医生为了钱,可以见死不救,除非你底下塞够了红包;老师为了钱,可以在课堂上只讲一半,另一半得交钱上他们自己家 里开的课后补习班......;而男人们为了所谓的事业,可以理直气壮地把老婆孩子丢在家里,没天没夜地在外面花天酒地地鬼混,美其名曰:应酬! 家里红旗不倒,家外彩旗飘飘,竟成了成功男人的必要条件与象征
这个社会中的男男女女都极其好面子,爱炫耀,并且善于抓住任何 可以抓住的机会向别人,往往是陌生人,表现自己如何重要,如何身份特别,地位崇高,如何与众不同.你可以随便在一家咖啡馆里听到临座的两个人高声地谈论自 己如何正在做着上千万,上亿万元的某个项目,一边用眼角的余辉探视是否引来了周围敬慕的眼神;便是坐公车,你也可以听到身后两个人点名道姓地大声议论着自 己公司里某某如何愚蠢之极,幸亏自己英明能干才替公司做下了几百万的单子;那说话的音量,其实是有意要当做稿子拿到中央人民广播电台向全世界广播的
一次乘飞机从杭州到北京,身后坐着一位不知道何等来历的中国人,想必自己以为应是有点钱, 或是有些权的.从登上飞机的一刻到最后下了飞机的一秒,一路上全机舱里就听他大着嗓门哇啦哇啦地不停,把空中小姐呼来唤去地指挥得团团转,仿佛是在使唤他 自己的私家女佣,神气活现地,觉得自己特有身份,有脸面.其实让人看着十足地缺乏教养,浅薄可笑.我就忍不住想,如果他真是那么大牌,何不买个头等舱的位 子,坐到前面让空中小姐好生伺候着,也般配他有钱有地位的身份,却要挤在普通舱里拿腔做势,真是让人看着莫名其妙.可以想象这样的人,平时走在外面是如何 自以为是,迈起步子来,一定会以为屁股下面至少抬着八乘的大轿
这样的情景在各地我都时常碰到,尤其是在餐馆里,更是经常 看到一些人,穿着人模人样,可一张嘴招呼服务员,那架式就象是奴隶主在吆喝自己的家奴,声音比那旧时为官老爷在前面开道的衙役还凶猛.可周围的人们似乎并 不以为奇,估计是司空见惯了.据说这样才特别能章显出自己是个大爷的身份,请客时在客人面前也显得面子十足
而下面的这次的经历,则让我深切地体会到,在中国,人与人之间存在着多么可怕的心理鸿沟
一次去杭州办事,有半天的空闲,便独自拿了相机到西湖边散步,随手拍拍西湖的风景.这时,看到前面一对年轻男女,互相轮流着在一个景点前面拍照,从 言谈举止看,应该是一对新婚夫妇出来度蜜月.心想,一对新人出来一趟,这样互相照相竟不能留个合影,多可惜.便走上前去,指着那男人手中的相机问道:要不 要我帮你们拍个合影?这样的事情在美国是非常平常的.无论你到哪里游玩,如果你是几个人在互相照相留影,总会有人从旁边经过时友善地问,需不需要帮你们一 起拍个合影.常常有人这样帮我,我也常常这样帮助别人.可令我万分尴尬的是,那两人听了我的问话之后,立即惊鄂地圆睁了眼睛看着我,满脸的疑虑,将我从头 到脚很戒备地打量了一番之后,一步一回头,将手中的相机紧紧地抱在怀里匆匆地走了.我楞了半晌,才突然明白了发生了什么,不由地苦笑了.看看自己手中的相 机,怎么着也得比他们的要贵好几倍的吧!
这件事时常让我想起,让我感叹,是什么让他们对别人的友善带着仿佛已经成为第二天性的怀疑,戒备甚至恐惧呢?
这个问题,在另一次足以表现我是如何成了不可救药的"美国大傻瓜"的事件之后,让我多少获得了一些答案
事情是这样的,还是在杭州.一次去那里办事,住在世贸大厦酒店,早上到楼下吃早餐,刚坐下, 临桌便有两个和尚热情地招呼我与我聊天.我正一个人怪无聊的,便与他们攀谈起来.这两个和尚自称是从五台山来的.五台山我听过,那里的和尚很有名,至少历 史上如此,于是我便对他们生了些好感.这样聊着聊着,两人便讲起了他们如何来到了杭州,一路如何辛苦,然后便讲他们的大师傅如何得了病,治病把身上的钱全 花光了,使他们不得不滞留此地回不了家,只好四处向人化缘筹集回去的路费.最后就说到我了,说能碰到我并和我这样开心地聊天,可见我很有佛缘,并说一看就 知道我心地善良,然后便请求我发发善心帮帮他们.我虽然对各式宗教向来抱着敬鬼神而远之的态度,但对佛教多少还是有些偏爱的.尤其是两位长老话说得如此诚 恳,又一脸真诚坦然地看着我的眼睛夸我,让我的虚荣心十分受用的同时,便觉得如果不有所帮助的表示,就真是说不过去了.适逢身上已经没有多少人民币, 没多想,便从钱包里拿了一张一百元的美钞给了他们,问可不可以?两人不动声色地接了,向我的钱包里瞥了一眼,说,能不能再多给一张.这一问,反让我觉得有 些蹊跷了,心里瞬间闪过一念:出家之人不知道感谢怎么可以这么贪?便和颜拒绝了,没再多想
两人匆匆又吃了几口饭,便起身告辞.我也吃完了,跟在他们身后出去
这时餐厅的领班走了过来与我搭话,问那两个和尚是不是向我要钱了,当知道我给了他们一百美元后,立即让门口的服务员通知楼下的警卫追了出去.我正一 头雾水,不知道发生了什么,领班告诉我,这两个人其实是骗子,已经在这里多日了.因为他们正正当当地买了餐卷进来吃饭,又看我与他们聊得很开心,便不好过 来打挠提醒我. 既然我是酒店的房客,现在知道"和尚"拿了我的钱,就要为我追回损失.果然,等领班带着我走到楼下时,那两个"和尚"已在正要上出租车前被追了回来,领班 把我的一百美元拿回来给我,让我赶紧离开.至于后来那两个"和尚"如何处置,我就不得而知了
事后向杭州当地的朋友提起,他差一点儿笑得背过了气,道:就你们这些美国回来的大傻瓜才会上这样的当!让我觉得,这人世间的几十年真是白活了
记得当年刚到美国时,常与几个朋友嘲笑美国人如何大脑简单,呆笨无比,一点都不知道转弯.想不到二十多年下来,我自己反到成了中国人眼里的美国大傻瓜,笨得不可理喻
在美国的生活,其实真是很单纯,平日从来不会想到有人会成心地骗你,大家说话办事也都直来直去,就事论事,用不着天天花时间精力说半截话,或是揣摩 别人一句话后面是否还有其他的更深的含意,更不用说走到外面还要时时刻刻提心吊胆地防着别人费尽心思设了圈套来坑你.这样的生活,能不让人变笨吗!
只是,我现在不再嘲笑美国人如何笨了,而更是觉得,生活在中国当今的社会之中,中国人聪明得可怕而且可悲
而美国式的呆笨碰到中国式的聪明,有时候所产生的效果却非常具有黑色幽默的味道
这是我西雅图的朋友在北京的一次经历
一次去中国出差,走在北京的街道上,我的这位朋友突然看到前面一个人掉了一个钱包.秉持着美国式的实在,我的朋友马上过去捡了起来,一边喊着前面的人就 追了上去,而那掉了钱包的人却似乎没有听见,反而脚步越来越快,于是我的朋友也加快了脚步匆匆往前赶.这时,从路旁一条偏街里就冲出一个人来,做着手势把 他拦下,叫他不要声张,指着他手中的钱包说,看有多少钱,两人分了得了;我的朋友一听这话,哪里同意,义正词严地批评他怎么可以如此没有道德良心,贪别人 的便宜,甩下他继续追赶那丢了钱包的人.那人终于被追上了,收回了钱包,却并没有任何感激的表现,反到有些不耐烦的样子,让我的朋友十分诧异不解;后来将 这件事向当地公司的人说了,经过点醒,才明白,那两个人原来是同伙,专门在街上做套坑人的.譬如,那钱包里也许只有两百块钱,如果你贪便宜同意和后面那人 分了,一人拿了一百,你这里正分着呢,那丢钱包的人这时就会非常适时地折了回来,把你们两人抓个正着.那与你分钱的人就会顺势一副改邪归正息事宁人的样 子,从口袋里掏出几白或几千元来(要看你有多少的油水可揩),声称这是他分到的一半,如数归换,而你之前分到的一半,现在却要变成了几百或几千才能还清 了,否则人证物证俱在,只好叫警察来解决
这种中国式的聪明机关得以成功的关键在于人们对不义之财的贪婪,据说这样的套子成功率极高,不想碰到了我这位在外面生活了十几年的美国大傻瓜,却竟然让那两个骗子徒劳无功.那两人看着我朋友远去的背影,估计一定会哭笑不得,恨得牙根发痒以为出门看错了黄历的
仔细想一想,之所以中国会有这样的坑骗招数,其实不也正说明了社会上有太多贪图不义之财的人,才使他们的伎俩有实施的市场吗?不是自己的东西,不可 以拿,这难道不应该是从小父母对孩子们最起码的做人的教育吗?怎么竟会有那么多的成年人能够忘记这个基本教育而使骗子们得以成功呢?
我知道写这篇文章是会被国内的中国人骂的.其实这本身也是如今中国让我感到叹息的另一方面:中国人不能容忍别人批评.你要是说中国一点的不好,那你 不是别有用心,就是假洋鬼子.至于是不是真的不好,则不在考虑之列.即便真的不好,他也一定会列出无数别人也如何不好来为自己辩护.也有人会说:你以为你 在外面时间长了,就自己觉得了不起了,中国这也不是那也不是,你算个什么东西!其实,我算什么东西不重要,也不是这里谈论的焦点.重要的是就事论事.谁能 讲我说的不是事实吗?如果不是心里还有着中国,我完全可以象个局外人一样,对中国的一切缺陷, 幸灾乐祸地当热闹看,何必费这么多的口舌
一个民族,不能正视自己的不足而妄自尊大,与奴颜婢膝,妄自菲薄都同样可悲
这篇文章的内容已经在心中积蓄很久了,不是一两天,也不是一两个月.一直难以下笔,实在是因为自己也是被骂者的同 类,损敌一千,自伤八百.无奈最后水满自溢, 还是忍不住从脑子里破堤而出,落在了笔端.把草稿拿给几个朋友看,有的说好,中肯;也有的说我太刻薄,伤人.也有的说:你找死啊?写这样的东西!就让我心 里特犹豫,要不要发出来啊?最后就借着点酒,贴了.酒壮SONG_二声(这个字的中文到底怎么写啊?字典里查不出来)人胆,一点不假.只是脑子里一直闪现 着儿时看过的一场电影,里面的主角对着步话机大声喊:向我开炮! 这几句话算是前言吧!
到中国旅游,本是一件非常愉快的事情,尤其带着儿子,让他们从小能够切身体会一下中国的风土人情,到各个历史景点感受一下中国的文化传承,真是胜过书本上一万个对长城,故宫,兵马佣介绍的文字与图片
只是,有所得也必有所失.在让儿子去感受中国悠久历史文化的熏陶的同时,也无可避免地会让他们目睹着当今中国社会各式各样的丑行,弄得儿子常常向我 提一些令我尴尬不知如何回答的问题.譬如,为什么街上的气车从来不让行人?为什么到处都那么脏,大家随便往地上扔东西? 为什么人们那么粗鲁没有礼貌?为什么又脏又臭的厕所门口总会有人收钱?为什么人们讲话那么大声好象在吵架?为什么那么多的人不分场合在哪里都抽烟?为什么 每到一个地方总有那么多的人扑过来非要卖东西给你而且缠着不走?其实答案不是没有,只是我不想说,因为我不愿意让他们在心中种下太多对中国负面的印象,尽 管我知道我的努力最终可能仍会是徒劳
孩子很小的时候,我们就开始带他们往中国跑了,目的是趁他们年纪还小,还能够对我们 的安排没有提出异议时,让他们尽早地习惯中国的状况.因为我们看到周围很多的朋友,等到孩子十几岁了,认为懂事了,有理解能力,能够吸收一路的所见所闻 了,于是带着去中国,满怀期望地想让孩子去感受中国的历史与文化,去了解自己作为中国人的根,而结果却往往是趁兴而去,扫兴而归.最典型的效果就是,回来 后孩子们做总结一般地对父母说:那就是你们出生长大的地方啊!语气中带着明显的失望与不屑,并拒绝以后再去.这个时候,弄得做父母的一只手伸了起来,不知 道是应该抽孩子的嘴巴,还是往自己脸上煽
中国这几十年经济发展突飞猛进,全世界都有目共睹.譬如说上海,几个月不去,就会展 现出一片崭新的市容.记得95年去上海,当空中小姐宣布我们已经飞临上海的天空时,我从飞机上向下望去,看到的只是一片漆黑.当我的兄弟接上我, 穿过无灯的黑暗,驱车行驶在上海市区那坑坑凹凹高低不平,恨不得能把肠子都颠腾出来的的街道上时,夜色之中,我看到的上海完全是一个庞大无比的建筑工地, 道路两旁以至绵延到天边的全是高耸入云的脚手架印在空中的影子;几年后再去上海,夜幕之下,我发现它已经完全成了灯火通明,高楼成群的花花世界了,比纽约 还要气势!当我一次从上海绕道香港回到美国,向太太描绘这这个崭新的世界时,太太凭着她八十年代的记忆,完全没有能力接受,这个在她嘴里一直是个”破上 海”的地方都快比她的香港还要繁华了.当然,如果我要是告诉她,上海外滩旁边的停车场里帮司机寻找车位的老头,身上的西服与领带比微软总裁比尔.盖兹穿得 还要正式气派,那还不如告诉她,我从上海到香港其实是脚踏着阿拉伯人的地毯而不是买票坐的飞机 ,所以我没有提起
遗憾的是,中国的经济发展,人们物质生活水平的提高,并没有相应地带来社会道德的提升.和谐社会的口号之所以如此响亮地提出,也同样响亮地说明,这个社会多么缺少和谐
这几年往中国跑了不知道多少次了,以我个人的经历所总结出来的这个社会的状况让我实在不敢恭维.这个社会缺少人与人之间的基本的尊敬,缺少人与人之 间的起码的信任,更缺少人与人之间最根本的平等相处的观念.古人曾说:仓廪实而知礼节.看着如今的中国社会, 我只能说,我们的古人太天真善良了
在中国,我每每看到公司里的主管面对下属,如何以在美国完全可以被视为人身攻击的方式进行训斥和辱骂,而同一个下属当他/她点头哈腰地承受了上司如 此的辱骂之后,转过身去便将同样的待遇抛给他/她的下属;而在街头上,则更不用说了.我在北京中关村,曾目击过一个警察如何象流氓一样欺辱讹诈一个骑板车 的民工,而这个民工却自始至终满脸谗笑不敢回一句话;也在浙江义乌的火车站,看到另一个骑板车的民工如何凶蛮地当着众人的面,狠狠地抽一个应该是比他地位 更底的刚进城的乡下人耳光
我有时与朋友开玩笑道:中国是一个从上往下煽耳光,从下往上磕头的社会,这个社会里人们没有平等,据说已经消灭了阶级,但却充满了无数等级森严贵贱分明的阶层
为了不用磕头而可以坚定地站到煽耳光的行列之中,这个社会充斥着种种的荒诞:
这个社会造就了每个人出门时,无论时间场合,都要穿上最漂亮最贵重的衣服,以在公众场合显示自己很有身份,从而获取别人的尊重;
这个社会造就了即便上班骑车也不过十分钟,开车却要堵半个小时,而仍然前仆后继争相购买私家车的人群,以显示自己富有与高人一等;
这个社会造就了全民族的小心谨慎,永远带着怀疑的眼光审视着周围的人群,害怕被骗,也常常被骗,有了机会也毫不迟疑地去骗别的傻瓜以显示自己的机警与聪明;
这个社会造就了全民族的狗眼病,在与别人的初次接触时, 每个人都隔着大脑中的门缝细心揣摩对方的身价与身份,在自己心中暗暗排列高低的档位,然后逐一划归属于要向他/她磕头的一族,或是将来有机会可以煽耳光的一类;
这个社会造就出与人交往时,如果你客气礼貌地对人说话,人家定会以为你身份卑微,或者有求于人,于是对你横眉竖眼,不屑正视;而你故意扯起了嗓子,一副土匪的样子高声吆喝,别人却会立即对你点头哈腰,唯唯喏喏,生怕一不小心得罪了不知道有着什么背景的何方神圣
这个社会造就了另一个严重的被称之为红眼病的流行病,每个人都觉得别人比自己挣到了更多的钱,于是每个人都削尖了脑袋挖尽心思要比别人捞更多的钱, 生活的重心仿佛除了钱还是钱.商人为了钱,可以黑着心卖没有营养的婴儿奶粉,让无数喝了它的婴儿终生残疾;农民为了钱,可以用各种化学原料施于水果之中让 它们显得鲜嫩可口,让吃过的人中毒至癌;医生为了钱,可以见死不救,除非你底下塞够了红包;老师为了钱,可以在课堂上只讲一半,另一半得交钱上他们自己家 里开的课后补习班......;而男人们为了所谓的事业,可以理直气壮地把老婆孩子丢在家里,没天没夜地在外面花天酒地地鬼混,美其名曰:应酬! 家里红旗不倒,家外彩旗飘飘,竟成了成功男人的必要条件与象征
这个社会中的男男女女都极其好面子,爱炫耀,并且善于抓住任何 可以抓住的机会向别人,往往是陌生人,表现自己如何重要,如何身份特别,地位崇高,如何与众不同.你可以随便在一家咖啡馆里听到临座的两个人高声地谈论自 己如何正在做着上千万,上亿万元的某个项目,一边用眼角的余辉探视是否引来了周围敬慕的眼神;便是坐公车,你也可以听到身后两个人点名道姓地大声议论着自 己公司里某某如何愚蠢之极,幸亏自己英明能干才替公司做下了几百万的单子;那说话的音量,其实是有意要当做稿子拿到中央人民广播电台向全世界广播的
一次乘飞机从杭州到北京,身后坐着一位不知道何等来历的中国人,想必自己以为应是有点钱, 或是有些权的.从登上飞机的一刻到最后下了飞机的一秒,一路上全机舱里就听他大着嗓门哇啦哇啦地不停,把空中小姐呼来唤去地指挥得团团转,仿佛是在使唤他 自己的私家女佣,神气活现地,觉得自己特有身份,有脸面.其实让人看着十足地缺乏教养,浅薄可笑.我就忍不住想,如果他真是那么大牌,何不买个头等舱的位 子,坐到前面让空中小姐好生伺候着,也般配他有钱有地位的身份,却要挤在普通舱里拿腔做势,真是让人看着莫名其妙.可以想象这样的人,平时走在外面是如何 自以为是,迈起步子来,一定会以为屁股下面至少抬着八乘的大轿
这样的情景在各地我都时常碰到,尤其是在餐馆里,更是经常 看到一些人,穿着人模人样,可一张嘴招呼服务员,那架式就象是奴隶主在吆喝自己的家奴,声音比那旧时为官老爷在前面开道的衙役还凶猛.可周围的人们似乎并 不以为奇,估计是司空见惯了.据说这样才特别能章显出自己是个大爷的身份,请客时在客人面前也显得面子十足
而下面的这次的经历,则让我深切地体会到,在中国,人与人之间存在着多么可怕的心理鸿沟
一次去杭州办事,有半天的空闲,便独自拿了相机到西湖边散步,随手拍拍西湖的风景.这时,看到前面一对年轻男女,互相轮流着在一个景点前面拍照,从 言谈举止看,应该是一对新婚夫妇出来度蜜月.心想,一对新人出来一趟,这样互相照相竟不能留个合影,多可惜.便走上前去,指着那男人手中的相机问道:要不 要我帮你们拍个合影?这样的事情在美国是非常平常的.无论你到哪里游玩,如果你是几个人在互相照相留影,总会有人从旁边经过时友善地问,需不需要帮你们一 起拍个合影.常常有人这样帮我,我也常常这样帮助别人.可令我万分尴尬的是,那两人听了我的问话之后,立即惊鄂地圆睁了眼睛看着我,满脸的疑虑,将我从头 到脚很戒备地打量了一番之后,一步一回头,将手中的相机紧紧地抱在怀里匆匆地走了.我楞了半晌,才突然明白了发生了什么,不由地苦笑了.看看自己手中的相 机,怎么着也得比他们的要贵好几倍的吧!
这件事时常让我想起,让我感叹,是什么让他们对别人的友善带着仿佛已经成为第二天性的怀疑,戒备甚至恐惧呢?
这个问题,在另一次足以表现我是如何成了不可救药的"美国大傻瓜"的事件之后,让我多少获得了一些答案
事情是这样的,还是在杭州.一次去那里办事,住在世贸大厦酒店,早上到楼下吃早餐,刚坐下, 临桌便有两个和尚热情地招呼我与我聊天.我正一个人怪无聊的,便与他们攀谈起来.这两个和尚自称是从五台山来的.五台山我听过,那里的和尚很有名,至少历 史上如此,于是我便对他们生了些好感.这样聊着聊着,两人便讲起了他们如何来到了杭州,一路如何辛苦,然后便讲他们的大师傅如何得了病,治病把身上的钱全 花光了,使他们不得不滞留此地回不了家,只好四处向人化缘筹集回去的路费.最后就说到我了,说能碰到我并和我这样开心地聊天,可见我很有佛缘,并说一看就 知道我心地善良,然后便请求我发发善心帮帮他们.我虽然对各式宗教向来抱着敬鬼神而远之的态度,但对佛教多少还是有些偏爱的.尤其是两位长老话说得如此诚 恳,又一脸真诚坦然地看着我的眼睛夸我,让我的虚荣心十分受用的同时,便觉得如果不有所帮助的表示,就真是说不过去了.适逢身上已经没有多少人民币, 没多想,便从钱包里拿了一张一百元的美钞给了他们,问可不可以?两人不动声色地接了,向我的钱包里瞥了一眼,说,能不能再多给一张.这一问,反让我觉得有 些蹊跷了,心里瞬间闪过一念:出家之人不知道感谢怎么可以这么贪?便和颜拒绝了,没再多想
两人匆匆又吃了几口饭,便起身告辞.我也吃完了,跟在他们身后出去
这时餐厅的领班走了过来与我搭话,问那两个和尚是不是向我要钱了,当知道我给了他们一百美元后,立即让门口的服务员通知楼下的警卫追了出去.我正一 头雾水,不知道发生了什么,领班告诉我,这两个人其实是骗子,已经在这里多日了.因为他们正正当当地买了餐卷进来吃饭,又看我与他们聊得很开心,便不好过 来打挠提醒我. 既然我是酒店的房客,现在知道"和尚"拿了我的钱,就要为我追回损失.果然,等领班带着我走到楼下时,那两个"和尚"已在正要上出租车前被追了回来,领班 把我的一百美元拿回来给我,让我赶紧离开.至于后来那两个"和尚"如何处置,我就不得而知了
事后向杭州当地的朋友提起,他差一点儿笑得背过了气,道:就你们这些美国回来的大傻瓜才会上这样的当!让我觉得,这人世间的几十年真是白活了
记得当年刚到美国时,常与几个朋友嘲笑美国人如何大脑简单,呆笨无比,一点都不知道转弯.想不到二十多年下来,我自己反到成了中国人眼里的美国大傻瓜,笨得不可理喻
在美国的生活,其实真是很单纯,平日从来不会想到有人会成心地骗你,大家说话办事也都直来直去,就事论事,用不着天天花时间精力说半截话,或是揣摩 别人一句话后面是否还有其他的更深的含意,更不用说走到外面还要时时刻刻提心吊胆地防着别人费尽心思设了圈套来坑你.这样的生活,能不让人变笨吗!
只是,我现在不再嘲笑美国人如何笨了,而更是觉得,生活在中国当今的社会之中,中国人聪明得可怕而且可悲
而美国式的呆笨碰到中国式的聪明,有时候所产生的效果却非常具有黑色幽默的味道
这是我西雅图的朋友在北京的一次经历
一次去中国出差,走在北京的街道上,我的这位朋友突然看到前面一个人掉了一个钱包.秉持着美国式的实在,我的朋友马上过去捡了起来,一边喊着前面的人就 追了上去,而那掉了钱包的人却似乎没有听见,反而脚步越来越快,于是我的朋友也加快了脚步匆匆往前赶.这时,从路旁一条偏街里就冲出一个人来,做着手势把 他拦下,叫他不要声张,指着他手中的钱包说,看有多少钱,两人分了得了;我的朋友一听这话,哪里同意,义正词严地批评他怎么可以如此没有道德良心,贪别人 的便宜,甩下他继续追赶那丢了钱包的人.那人终于被追上了,收回了钱包,却并没有任何感激的表现,反到有些不耐烦的样子,让我的朋友十分诧异不解;后来将 这件事向当地公司的人说了,经过点醒,才明白,那两个人原来是同伙,专门在街上做套坑人的.譬如,那钱包里也许只有两百块钱,如果你贪便宜同意和后面那人 分了,一人拿了一百,你这里正分着呢,那丢钱包的人这时就会非常适时地折了回来,把你们两人抓个正着.那与你分钱的人就会顺势一副改邪归正息事宁人的样 子,从口袋里掏出几白或几千元来(要看你有多少的油水可揩),声称这是他分到的一半,如数归换,而你之前分到的一半,现在却要变成了几百或几千才能还清 了,否则人证物证俱在,只好叫警察来解决
这种中国式的聪明机关得以成功的关键在于人们对不义之财的贪婪,据说这样的套子成功率极高,不想碰到了我这位在外面生活了十几年的美国大傻瓜,却竟然让那两个骗子徒劳无功.那两人看着我朋友远去的背影,估计一定会哭笑不得,恨得牙根发痒以为出门看错了黄历的
仔细想一想,之所以中国会有这样的坑骗招数,其实不也正说明了社会上有太多贪图不义之财的人,才使他们的伎俩有实施的市场吗?不是自己的东西,不可 以拿,这难道不应该是从小父母对孩子们最起码的做人的教育吗?怎么竟会有那么多的成年人能够忘记这个基本教育而使骗子们得以成功呢?
我知道写这篇文章是会被国内的中国人骂的.其实这本身也是如今中国让我感到叹息的另一方面:中国人不能容忍别人批评.你要是说中国一点的不好,那你 不是别有用心,就是假洋鬼子.至于是不是真的不好,则不在考虑之列.即便真的不好,他也一定会列出无数别人也如何不好来为自己辩护.也有人会说:你以为你 在外面时间长了,就自己觉得了不起了,中国这也不是那也不是,你算个什么东西!其实,我算什么东西不重要,也不是这里谈论的焦点.重要的是就事论事.谁能 讲我说的不是事实吗?如果不是心里还有着中国,我完全可以象个局外人一样,对中国的一切缺陷, 幸灾乐祸地当热闹看,何必费这么多的口舌
一个民族,不能正视自己的不足而妄自尊大,与奴颜婢膝,妄自菲薄都同样可悲
淡鸟大师的红油和夫妻肺片(转贴)
俺这个号称“解密”, 其实也就是近两年来对这个菜反复捉摸后心得的一个总结,今天写出来希望能对大家功克这道菜有所帮助。 如果你真的知道这夫妻肺片的秘方,可千万不要吝啬!
不过俺一直怀疑这所谓秘方的存在,即便有,俺认为充其量也不过是各家各店的枝末变化而已。其实话说回来,有没有秘方并不重要,重要的是味道可不可以模仿,就像Cocacola, 没有秘方并不妨碍其他厂家配置出味道相近足以乱真的 XXcola来。
如 果说夫妻肺(废)片是最受广大食客欢迎的一道川菜,恐怕举手的人有不少。和其他几个流行川菜相比(如麻婆豆腐,宫宝鸡丁,水煮肉,辣子鸡等),夫妻肺片明 显是难度比较高的。虽然俺不敢说其他几味川菜没什么技术含量,起码能把这几个菜鼓捣得像模像样的大有人在。而夫妻肺片则不同,在国外即使在大城市最好的川 菜馆里恐怕也未必点得到让你满意的肺片。
“主料;牛肉,牛杂(肚,心,舌,头皮),辅料:红油,油酥花生,白卤水,复制酱油,芝麻,花椒 面,盐,味精,白酒.八角8只,花椒5克,桂皮10克包纱布袋,。做法:牛肉牛杂加卤水,盐,白酒75克煮料至熟而不烂.晾凉,片成4厘米长,2.6厘米 宽的薄片.加红油,卤水,复制酱油,盐,味精,芝麻花椒面,芹菜段伴匀.”这段文字据说是根据川菜大师陈松如的方子而来,大家随便到网上找找或者拿本川菜 图书翻翻,这夫妻肺片的做法基本上就是这样,差别不大。俺认为这方子虽然不错,可惜缺少了很多重要的细节,尤其是关于红油,味汁的调制。那么做好这道菜的 关键到底在哪呢?
根据俺的仔细研究和反复尝试,总结这道菜的调味关键有三个环节:红油,复合酱油,和卤汁的使用。
先说红 油。这个问题看到很多朋友讨论过,有人认为这红油的制作是不需要除辣椒外的任何调料的,亦无须长时间熬制。我认为这是把红油和油泼辣子混淆了。个人认为这 个红油是做好很多麻辣川味凉菜的首要关键,比如夫妻肺片和蒜泥白肉,这红油应含有多种香料的复合香气,浓郁而具有回味,而简单的油泼辣子是无法满足这种要 求的。这里顺便说一句,本人其实是油泼辣子的忠实拥护者,一直认为简单的油泼辣子(当然需要辣子新鲜优质)是真正的百吃不厌。只不过对于夫妻肺片来讲,油 泼辣子并不合适。
除气味以外,红油的另一个关键就在这个“红”字上,鲜红发亮的红油给人以感官的刺激,让人食欲大增。要是你调出的“红”油黄不黄白不白,那么拌出的肺片味道再好也要大打折扣了。
再 谈复合酱油。所谓复合酱油就是用多种香料调料与酱油混合熬制而成的再加工酱油,这个不是能直接从商店里买来的,需要你自己动手。酱油要尽量选用高质(废 话!)并且咸度较低的。因为经过较长时间熬制后的复制酱油比较浓稠,如果原料酱油本身过咸就不大合适了。复合酱油是这个夫妻肺片调味的另一关键,如果只用 简单的酱油(包括老抽生抽)这肺片任你大力咀嚼回味恐怕也是难以悠长滴。除调味外,复合酱油还起到附加的调色作用。
川菜馆子里的一盘夫妻肺片往往大半的牛肉牛杂都浸在红油里,诱人是不必说了,可这正是俺们这些妄想仿冒天下一切美食的家庭厨师们最头痛心痛的问题??有多少人在吃过那盘子里的片片之后动过要把那半盘红油端回家去的念头?反正我是有的。
那么那红彤彤油亮亮的真的都是红油么?
当然不是。这个不用说大家也知道??菜谱上不是明明白白写着么“加白卤水。。。”真正的问题是:这个卤水到底要加多少呢?这个恐怕心里有谱的就不多了。
经 过俺的反复试验,这卤水和红油的用量比例可以控制在大约1:1左右(当然这个比例是建立在一定的红油绝对用量上的),希望这个消息能减轻各位拌肺片时一半 的心痛:)不过,虽然掺了一半水,你看到的那半盘子红油倒差不多实实在在的全是红油,因为大部分的卤水都吸附在牛肉牛杂上了。较高量的使用卤水有两个好 处:1。使肺片充分入味;2。避免了肺片因吸附了太多的红油而过于油腻。
好,罗嗦了半天总算可以进入正题了:具体做法。为了大家易于掌握,俺特意“精确”度量了各种原配料的用量。 注意:“大勺”指Table Spoon, 这个度量比一般咱们家里用来喝汤吃饭的勺子要大一点; “小勺”指Tea Spoon.
一. 红油熬制:
原料:
这 个需要选用优质的辣椒面是没错的。看到网上有人讲红油要用几种不同种类的名贵辣椒如四川二金条云南小米椒等,按特定比例混合熬制,这些东西在国内也不一定 买得齐,咱们就更不敢奢求了:?)从实际角度出发, 韩国辣椒面是一个不错的选择,优点在于色泽红润自然,辣度适中,又哪里都买得到。
除辣椒外,我还用约十余种香料/调料,多是家里平时常用的,大家一般在中国超市里也买得到。下面这张图中,按从左到右,从上到下的次序依次是:
花 椒 (1大勺),丁香(4-6粒,这个味道强烈,不宜多放),桂皮(小指大小2-3块),小茴香(1小勺),白芝麻(1大勺),草果(1-2枚,用刀拍破), 八角(又称大料,大茴,3 ? 4 颗),紫草(1大勺),辣椒面 (1 Cup),香叶(2 ? 4 片),生姜(1块),葱白(数段)。
红油香料合影。

这里面除了紫草以外基本上都是中国菜最基本的调料。紫草是制作四川红油常用的一种天然色素,加强红油的红色,一般在国内的调料店或中药店买得到,我这个还是几年前托朋友从国内带来的。如果没有紫草也没有关系,单用韩国辣椒面也能有很好的效果。
桂皮没有就算了,千万不能用老美的cinnamon (肉桂) 代替,切记。
熬 制:将植物油2.5Cup(约500克,菜籽油为上选,可用大豆色拉油代替)锅中烧开,放置温凉后下葱白姜块,见到有细小的泡沫从姜葱四周升起时将炉火转 至最小,然后下入花椒,丁香,桂皮,小茴,草果,八角,香叶,紫草,辣椒面,搅拌匀,熬制30-40分钟,熬制期间时常搅拌一下,以防糊锅底。30-40 分钟后加入白芝麻继续熬制30-40分钟,关火。将熬好的红油晾至温凉后连油带料倒入一个大的玻璃量杯或其他带嘴的玻璃或瓷质容器中,用保鲜膜封好在冰箱 冷藏室内放置24-48小时以使辣椒面的辣味,红色,香料的香气进一步溶解于油中。同时找几个洗干净晾干的带盖玻璃瓶备用。
刚熬好的连油带料的红油,看上去颜色很深。

1-2天后将红油取出,这时你会看到除了香叶,葱段,花椒,八角 和稍许芝麻漂浮于油面外其他调味料都已经和辣椒面一起像淤泥一样牢牢地沉在油低,用筷子拣除浮在上面的香叶,葱段和八角,然后就可以轻松地把红油倒在事先准备好的玻璃瓶中。杯低的“淤泥”弃去不用。
从瓶口往下看,红油的颜色呈深棕红色。

透过阳光来看,两瓶诱人的红色。

补充说明:
1. 刚熬好的新鲜红油味道最佳,这样一次熬出的红油可以拌4-5次肺片(每次可拌3-5倍饭店里一盘量),用剩的最好放冰箱冷藏室保存,并且尽量在半个月内消 灭光。见过一本制作精美的西人编纂的中餐烹调书里白纸黑字写着这四川红油熬好了要封入瓶中60天后开封取用不由大笑,作者八成对于这红油和红酒的区别没太 搞清 :)
2. 三奈是红油增香的一种比较重要的香料,又名山奈,砂姜,沙姜。长相类似老姜,一般分新鲜的,切片晾干的或磨成粉的三种,大家若有幸在超市看到,千万不可客气,买来每次熬红油的时候放一点。
3. 红油香料的使用可以灵活一些,但是一个重要的原则是那些味道强烈、怪异的要少放或不放,如孜然,咖喱等是万万放不得的。
二. 复合酱油制作方法:
原料:优质酱油或生抽1 Cup, 老抽2大勺,白糖3大勺,红糖3大勺,其他调料与红油调料相仿(除辣椒面,紫草和芝麻外其他都要)。
制法:将酱油等各种原料放在一只小锅中,中火烧开后转最小火熬制40-60分钟,晾凉后将调味料取出倒入一个干净的玻璃瓶中备用。
补充说明:
1. 复制酱油熬制糖的重要性很高,熬出的成品应以咸为主但咸中回甜。红糖起到上色作用,使被卤汁稀释后的复制酱油色泽红润。白糖可以冰糖替代。
2. 熬制时锅不要盖盖,这样酱油中的一部分水分得以蒸发,使成品浓稠。比如我这次1Cup酱油熬了约1小时后还剩2/3多一点。
3. 向大家推荐两种优质酱油,第一个是台湾产的“万家香”牌陈年酱油,注意这种酱油有几种不同的包装,品质不尽相同,要买那种每桶64 FL OZ(1600 毫升)装的。此酱油在色泽和口味上都属上乘。第二个是美国产“万”字牌酱油(KIKKOMAN Soy Sauce),Costco有卖,1加仑铁桶装6-7刀,很划算,质量也不错,缺点是有点过咸。
三.关于卤水:
这里卤水指用来卤制牛肉牛杂的汤汁,不放酱油,所以是白卤水。因为我一般牛肚用的较多,卤制后的卤水腥味较大,所以在拌肺片时便改用以猪骨和整鸡熬制的高汤,效果更好。如没有高汤可用水1Cup, 鸡精、盐各一小勺,加姜片葱结烧开代替。
四. 好,终于可以进入夫妻肺片的正式制作:
1. 将牛肉牛杂切大块洗净后飞水。锅中加水没过牛肉,加料酒,姜块,葱结,八角,花椒,桂皮,小茴等香料大火煮开后转中小火炖至牛肉牛杂熟而微烂(more on this later), 捞出放晾,切薄片备用。
2. 关键部分来了!取一只大碗或小锅,里面放1/2Cup卤汁或高汤,加鸡精、精盐各1/2小勺(如果是用现烧的简易高汤替代品就不用再加鸡精和盐了),复制 酱油3大勺,花椒面1/2小勺,红油1/2Cup,麻油(香油)1大勺,花椒油1大勺搅拌匀后加入切好的牛肉牛杂250克,拌匀,装盘(最好用深盘或 碗),撒上油酥花生碎(去皮花生米油炸/炒酥黄后用刀压碎或blender打碎)、炒熟的白芝麻、香葱碎、芹菜末(用中国芹菜)和香菜末就可上桌了。
夫妻肺片

补充说明:
1. 传说中的牛头皮是买不到了,所以原料中的牛肉最好用牛腱(beef shank)代替,其他牛肚,牛心和牛舌都比较容易购得。牛腱和牛肚都富含胶质,在卤熟放凉后因胶质重新凝结而会变得很硬,所以要煮得烂一些。我一般都是 这两种一起放在高压锅中压至熟烂(约40-45分钟),放冰箱冷藏室中彻底冷却后取出切片。
2. 此红油/卤汁/牛肉牛杂的用量和比例可以确保你拌好的肺片在外观上达到professional 的效果。废片吃完后少量的补一些卤汁和复制酱油即可继续加入牛肉牛杂,如此可以反复添加至少3次牛肉牛杂而不改变成品的效果。注意每次添加的片片要比上一次略少。
3. 吃完后剩下的红油汤汁用来煮面或拌面味道奇佳。
4. 最后给大家推荐两种很好的花椒油,一个是“黎红”牌花椒油,另一个是“川老汇”牌花椒油,两种花椒油都是用著名的汉源花椒炼制而成,在国外很难买到优质的花椒,如果你能买到这两种花椒油,就可以一尝四川花椒的香麻了。
夹两片尝尝~~

总 之只要处理好红油、复合酱油、卤汁的调制和红油与卤汁的用量比例这几个环节,你就一定可以拌出具有专业水准的夫妻肺片了。每次俺请三五好友到家里来吃饭 时,干掉两斤牛肉牛杂是不成问题的,下次你和朋友一起potluck 时别忘了也拌一道夫妻肺片,俺担保你成为当天聚会最受欢迎的人!
再来片肚片!

后记:
其 实早想把这篇夫妻肺片写出来跟大家分享,不过一直没什么时间,于是东一下西一下地抠点零碎时间慢慢写了,结果一不小心凑成了这么一篇又臭又长的,其实我写 菜谱时有这个臭毛病,总想把自己的经验心得尽可能的仔细描述出来,所以难免显得有些婆婆妈妈(各位私房女同胞不要多心,俺用这个词纯粹是因为这是一个约定 俗成的说法,便同夫妻肺片里未必有“肺”一样, :)),即便如此,我做梦也没想到一个菜谱可以写这么长,只好谢谢大家的耐心了~~
不过俺一直怀疑这所谓秘方的存在,即便有,俺认为充其量也不过是各家各店的枝末变化而已。其实话说回来,有没有秘方并不重要,重要的是味道可不可以模仿,就像Cocacola, 没有秘方并不妨碍其他厂家配置出味道相近足以乱真的 XXcola来。
如 果说夫妻肺(废)片是最受广大食客欢迎的一道川菜,恐怕举手的人有不少。和其他几个流行川菜相比(如麻婆豆腐,宫宝鸡丁,水煮肉,辣子鸡等),夫妻肺片明 显是难度比较高的。虽然俺不敢说其他几味川菜没什么技术含量,起码能把这几个菜鼓捣得像模像样的大有人在。而夫妻肺片则不同,在国外即使在大城市最好的川 菜馆里恐怕也未必点得到让你满意的肺片。
“主料;牛肉,牛杂(肚,心,舌,头皮),辅料:红油,油酥花生,白卤水,复制酱油,芝麻,花椒 面,盐,味精,白酒.八角8只,花椒5克,桂皮10克包纱布袋,。做法:牛肉牛杂加卤水,盐,白酒75克煮料至熟而不烂.晾凉,片成4厘米长,2.6厘米 宽的薄片.加红油,卤水,复制酱油,盐,味精,芝麻花椒面,芹菜段伴匀.”这段文字据说是根据川菜大师陈松如的方子而来,大家随便到网上找找或者拿本川菜 图书翻翻,这夫妻肺片的做法基本上就是这样,差别不大。俺认为这方子虽然不错,可惜缺少了很多重要的细节,尤其是关于红油,味汁的调制。那么做好这道菜的 关键到底在哪呢?
根据俺的仔细研究和反复尝试,总结这道菜的调味关键有三个环节:红油,复合酱油,和卤汁的使用。
先说红 油。这个问题看到很多朋友讨论过,有人认为这红油的制作是不需要除辣椒外的任何调料的,亦无须长时间熬制。我认为这是把红油和油泼辣子混淆了。个人认为这 个红油是做好很多麻辣川味凉菜的首要关键,比如夫妻肺片和蒜泥白肉,这红油应含有多种香料的复合香气,浓郁而具有回味,而简单的油泼辣子是无法满足这种要 求的。这里顺便说一句,本人其实是油泼辣子的忠实拥护者,一直认为简单的油泼辣子(当然需要辣子新鲜优质)是真正的百吃不厌。只不过对于夫妻肺片来讲,油 泼辣子并不合适。
除气味以外,红油的另一个关键就在这个“红”字上,鲜红发亮的红油给人以感官的刺激,让人食欲大增。要是你调出的“红”油黄不黄白不白,那么拌出的肺片味道再好也要大打折扣了。
再 谈复合酱油。所谓复合酱油就是用多种香料调料与酱油混合熬制而成的再加工酱油,这个不是能直接从商店里买来的,需要你自己动手。酱油要尽量选用高质(废 话!)并且咸度较低的。因为经过较长时间熬制后的复制酱油比较浓稠,如果原料酱油本身过咸就不大合适了。复合酱油是这个夫妻肺片调味的另一关键,如果只用 简单的酱油(包括老抽生抽)这肺片任你大力咀嚼回味恐怕也是难以悠长滴。除调味外,复合酱油还起到附加的调色作用。
川菜馆子里的一盘夫妻肺片往往大半的牛肉牛杂都浸在红油里,诱人是不必说了,可这正是俺们这些妄想仿冒天下一切美食的家庭厨师们最头痛心痛的问题??有多少人在吃过那盘子里的片片之后动过要把那半盘红油端回家去的念头?反正我是有的。
那么那红彤彤油亮亮的真的都是红油么?
当然不是。这个不用说大家也知道??菜谱上不是明明白白写着么“加白卤水。。。”真正的问题是:这个卤水到底要加多少呢?这个恐怕心里有谱的就不多了。
经 过俺的反复试验,这卤水和红油的用量比例可以控制在大约1:1左右(当然这个比例是建立在一定的红油绝对用量上的),希望这个消息能减轻各位拌肺片时一半 的心痛:)不过,虽然掺了一半水,你看到的那半盘子红油倒差不多实实在在的全是红油,因为大部分的卤水都吸附在牛肉牛杂上了。较高量的使用卤水有两个好 处:1。使肺片充分入味;2。避免了肺片因吸附了太多的红油而过于油腻。
好,罗嗦了半天总算可以进入正题了:具体做法。为了大家易于掌握,俺特意“精确”度量了各种原配料的用量。 注意:“大勺”指Table Spoon, 这个度量比一般咱们家里用来喝汤吃饭的勺子要大一点; “小勺”指Tea Spoon.
一. 红油熬制:
原料:
这 个需要选用优质的辣椒面是没错的。看到网上有人讲红油要用几种不同种类的名贵辣椒如四川二金条云南小米椒等,按特定比例混合熬制,这些东西在国内也不一定 买得齐,咱们就更不敢奢求了:?)从实际角度出发, 韩国辣椒面是一个不错的选择,优点在于色泽红润自然,辣度适中,又哪里都买得到。
除辣椒外,我还用约十余种香料/调料,多是家里平时常用的,大家一般在中国超市里也买得到。下面这张图中,按从左到右,从上到下的次序依次是:
花 椒 (1大勺),丁香(4-6粒,这个味道强烈,不宜多放),桂皮(小指大小2-3块),小茴香(1小勺),白芝麻(1大勺),草果(1-2枚,用刀拍破), 八角(又称大料,大茴,3 ? 4 颗),紫草(1大勺),辣椒面 (1 Cup),香叶(2 ? 4 片),生姜(1块),葱白(数段)。
红油香料合影。

这里面除了紫草以外基本上都是中国菜最基本的调料。紫草是制作四川红油常用的一种天然色素,加强红油的红色,一般在国内的调料店或中药店买得到,我这个还是几年前托朋友从国内带来的。如果没有紫草也没有关系,单用韩国辣椒面也能有很好的效果。
桂皮没有就算了,千万不能用老美的cinnamon (肉桂) 代替,切记。
熬 制:将植物油2.5Cup(约500克,菜籽油为上选,可用大豆色拉油代替)锅中烧开,放置温凉后下葱白姜块,见到有细小的泡沫从姜葱四周升起时将炉火转 至最小,然后下入花椒,丁香,桂皮,小茴,草果,八角,香叶,紫草,辣椒面,搅拌匀,熬制30-40分钟,熬制期间时常搅拌一下,以防糊锅底。30-40 分钟后加入白芝麻继续熬制30-40分钟,关火。将熬好的红油晾至温凉后连油带料倒入一个大的玻璃量杯或其他带嘴的玻璃或瓷质容器中,用保鲜膜封好在冰箱 冷藏室内放置24-48小时以使辣椒面的辣味,红色,香料的香气进一步溶解于油中。同时找几个洗干净晾干的带盖玻璃瓶备用。
刚熬好的连油带料的红油,看上去颜色很深。

1-2天后将红油取出,这时你会看到除了香叶,葱段,花椒,八角 和稍许芝麻漂浮于油面外其他调味料都已经和辣椒面一起像淤泥一样牢牢地沉在油低,用筷子拣除浮在上面的香叶,葱段和八角,然后就可以轻松地把红油倒在事先准备好的玻璃瓶中。杯低的“淤泥”弃去不用。
从瓶口往下看,红油的颜色呈深棕红色。

透过阳光来看,两瓶诱人的红色。

补充说明:
1. 刚熬好的新鲜红油味道最佳,这样一次熬出的红油可以拌4-5次肺片(每次可拌3-5倍饭店里一盘量),用剩的最好放冰箱冷藏室保存,并且尽量在半个月内消 灭光。见过一本制作精美的西人编纂的中餐烹调书里白纸黑字写着这四川红油熬好了要封入瓶中60天后开封取用不由大笑,作者八成对于这红油和红酒的区别没太 搞清 :)
2. 三奈是红油增香的一种比较重要的香料,又名山奈,砂姜,沙姜。长相类似老姜,一般分新鲜的,切片晾干的或磨成粉的三种,大家若有幸在超市看到,千万不可客气,买来每次熬红油的时候放一点。
3. 红油香料的使用可以灵活一些,但是一个重要的原则是那些味道强烈、怪异的要少放或不放,如孜然,咖喱等是万万放不得的。
二. 复合酱油制作方法:
原料:优质酱油或生抽1 Cup, 老抽2大勺,白糖3大勺,红糖3大勺,其他调料与红油调料相仿(除辣椒面,紫草和芝麻外其他都要)。
制法:将酱油等各种原料放在一只小锅中,中火烧开后转最小火熬制40-60分钟,晾凉后将调味料取出倒入一个干净的玻璃瓶中备用。
补充说明:
1. 复制酱油熬制糖的重要性很高,熬出的成品应以咸为主但咸中回甜。红糖起到上色作用,使被卤汁稀释后的复制酱油色泽红润。白糖可以冰糖替代。
2. 熬制时锅不要盖盖,这样酱油中的一部分水分得以蒸发,使成品浓稠。比如我这次1Cup酱油熬了约1小时后还剩2/3多一点。
3. 向大家推荐两种优质酱油,第一个是台湾产的“万家香”牌陈年酱油,注意这种酱油有几种不同的包装,品质不尽相同,要买那种每桶64 FL OZ(1600 毫升)装的。此酱油在色泽和口味上都属上乘。第二个是美国产“万”字牌酱油(KIKKOMAN Soy Sauce),Costco有卖,1加仑铁桶装6-7刀,很划算,质量也不错,缺点是有点过咸。
三.关于卤水:
这里卤水指用来卤制牛肉牛杂的汤汁,不放酱油,所以是白卤水。因为我一般牛肚用的较多,卤制后的卤水腥味较大,所以在拌肺片时便改用以猪骨和整鸡熬制的高汤,效果更好。如没有高汤可用水1Cup, 鸡精、盐各一小勺,加姜片葱结烧开代替。
四. 好,终于可以进入夫妻肺片的正式制作:
1. 将牛肉牛杂切大块洗净后飞水。锅中加水没过牛肉,加料酒,姜块,葱结,八角,花椒,桂皮,小茴等香料大火煮开后转中小火炖至牛肉牛杂熟而微烂(more on this later), 捞出放晾,切薄片备用。
2. 关键部分来了!取一只大碗或小锅,里面放1/2Cup卤汁或高汤,加鸡精、精盐各1/2小勺(如果是用现烧的简易高汤替代品就不用再加鸡精和盐了),复制 酱油3大勺,花椒面1/2小勺,红油1/2Cup,麻油(香油)1大勺,花椒油1大勺搅拌匀后加入切好的牛肉牛杂250克,拌匀,装盘(最好用深盘或 碗),撒上油酥花生碎(去皮花生米油炸/炒酥黄后用刀压碎或blender打碎)、炒熟的白芝麻、香葱碎、芹菜末(用中国芹菜)和香菜末就可上桌了。
夫妻肺片

补充说明:
1. 传说中的牛头皮是买不到了,所以原料中的牛肉最好用牛腱(beef shank)代替,其他牛肚,牛心和牛舌都比较容易购得。牛腱和牛肚都富含胶质,在卤熟放凉后因胶质重新凝结而会变得很硬,所以要煮得烂一些。我一般都是 这两种一起放在高压锅中压至熟烂(约40-45分钟),放冰箱冷藏室中彻底冷却后取出切片。
2. 此红油/卤汁/牛肉牛杂的用量和比例可以确保你拌好的肺片在外观上达到professional 的效果。废片吃完后少量的补一些卤汁和复制酱油即可继续加入牛肉牛杂,如此可以反复添加至少3次牛肉牛杂而不改变成品的效果。注意每次添加的片片要比上一次略少。
3. 吃完后剩下的红油汤汁用来煮面或拌面味道奇佳。
4. 最后给大家推荐两种很好的花椒油,一个是“黎红”牌花椒油,另一个是“川老汇”牌花椒油,两种花椒油都是用著名的汉源花椒炼制而成,在国外很难买到优质的花椒,如果你能买到这两种花椒油,就可以一尝四川花椒的香麻了。
夹两片尝尝~~

总 之只要处理好红油、复合酱油、卤汁的调制和红油与卤汁的用量比例这几个环节,你就一定可以拌出具有专业水准的夫妻肺片了。每次俺请三五好友到家里来吃饭 时,干掉两斤牛肉牛杂是不成问题的,下次你和朋友一起potluck 时别忘了也拌一道夫妻肺片,俺担保你成为当天聚会最受欢迎的人!
再来片肚片!

后记:
其 实早想把这篇夫妻肺片写出来跟大家分享,不过一直没什么时间,于是东一下西一下地抠点零碎时间慢慢写了,结果一不小心凑成了这么一篇又臭又长的,其实我写 菜谱时有这个臭毛病,总想把自己的经验心得尽可能的仔细描述出来,所以难免显得有些婆婆妈妈(各位私房女同胞不要多心,俺用这个词纯粹是因为这是一个约定 俗成的说法,便同夫妻肺片里未必有“肺”一样, :)),即便如此,我做梦也没想到一个菜谱可以写这么长,只好谢谢大家的耐心了~~
Subscribe to:
Posts (Atom)